What is AES Encryption and How Does It Work [Detailed Guide]

Today we live in a world of data where humans produce around 2.5 quintillion bytes of data every day. For perspective, that is 2.5, followed by 18 zeros. With data being produced every day, there are bound to be security issues. Experts estimated the cost of an average data breach in 2021 to be around 4.24 million US dollars. The more alarming trend is that this cost is a 10% rise from 2019.
These are the times when you need robust security systems. A strong encryption system is the bedrock of a robust digital security system. Today we are going to talk about the advanced encryption standard, or AES, which has become the encryption standard of choice for institutions that manage sensitive data.
In this blog, we will throw some light on the following aspects of the AES encryption algorithm
- What is AES encryption?
- How secure is AES encryption?
- Why was the AES encryption algorithm necessary?
- Benefits of AES
- How does AES encryption work?
- Some examples of AES encryption
How Secure is AES Encryption?
The AES encryption algorithm is an algorithm that is really hard to crack. How hard? Experts estimate that breaking the encryption of AES with a brute-force attack would take more than 100 trillion years, even for the fastest supercomputer in the world. Even Quantum computers will take at least six months to break an AES algorithm.
Many experts consider AES to be one of the most secure encryption algorithms ever created. The creators of AES have made it publicly available. This creates suspicion in many people’s minds about how secure can an algorithm be if it’s open source. Another way of looking at this is that the makers of this algorithm are so confident that they released it to the public. Another thing worth noting is that right from Federal agencies to the military most of these organizations still use the AES encryption standard. If they stop using it, we might think something is wrong. But their continued use of the AES algorithm in cryptography suggests that everything is fine.
What is AES encryption?
The Advanced Encryption Standard, or AES, is a method for encrypting data in a way that is much stronger than traditional methods. The first version of the standard was released in 1996, and experts have improved it several times since then to meet the needs of today’s data security requirements. The basic premise of the AES standard is to use a series of rotations and substitutions to transform plaintext data into ciphertext. We know this process as encryption.
AES is a symmetric algorithm that uses the same key for encryption and decryption and originated as a design for military and government use. The key size is usually 128 bytes (16 bits) and is typically changed infrequently to provide maximum protection against brute force attacks.
The National Institute for Standards and Technology(NIST) is the government organization that is responsible for publishing and maintaining AES. In fact, AES is one of the many NIST-issued federal information processing standards. The US Secretary of Commerce approves all these standards before publication. The National Security Agency (NSA) approves AES as the sole available block cipher for transmitting secret information across government agencies.
The AES encryption online algorithm has become the cryptographic technology of choice for people who want to encrypt their data securely. Federal government agencies, as well as non-government agencies, use AES encryption daily in order to protect their sensitive data.
The following Is a graphical illustration of the AES algorithm at work
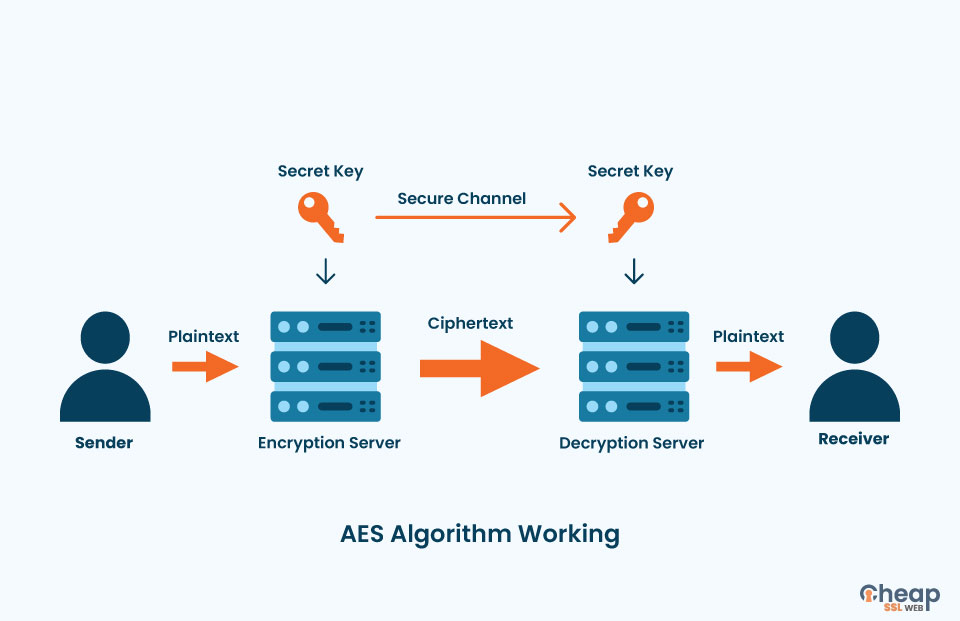
A sender sends a plain text file to an encryption server. We use an AES secret key on this server to encrypt the plain text data into ciphertext data. The receiver of the file can only read the contents of the file if he has the secret key to open the file.
Why Was the AES Encryption Algorithm necessary?
The DES (Data Encryption Standard) encryption algorithm was the predecessor to the AES encryption algorithm. While it sufficed for the needs of the generation of computers when it was created, with every passing year, hackers found it increasingly easy to break into the DES algorithm. We have shown that in the below image.
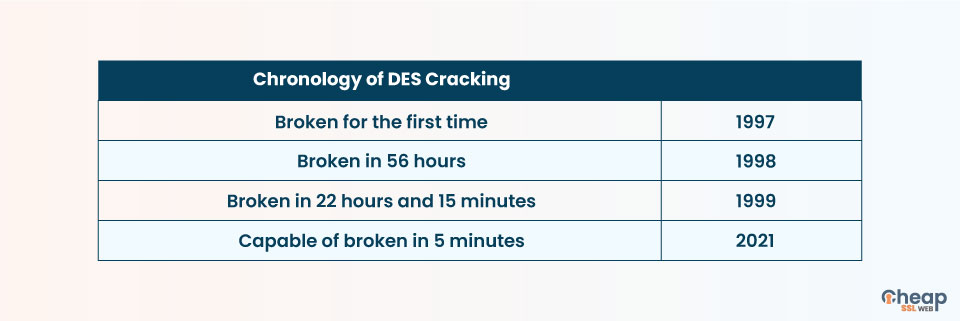
Thus the need for a stronger encryption algorithm arose. The security researchers first tried creating a triple DES algorithm. The things that did not work out as planned as the base of this algorithm was excruciatingly slow. Hence the researchers went in a new direction and decided to create an altogether new algorithm. AES has longer key sizes and stronger ciphers than the DES algorithm.
Benefits of the AES
- Ever since its inception, the AES algorithm has proven its worth as a reliable security mechanism. Here are some of the major benefits of using the AES algorithm
- Engineers can implement the AES algorithm both in software as well as hardware.
- The AES algorithm, being open-source, allows private and public sectors to access it.
- The AES algorithm is extremely resilient against hacking attempts.
- The AES encryption algorithm is the most widely used security protocol in the world today.
How does AES encryption work?
Here is a brief overview of how the AES encryption mechanism works. AES is known for its major design principle called the substitution permutation network. The substitution permutation network refers to a series of mathematical operations linked with each other. The network works by applying a lot of layers of substitution boxes and permutation boxes to play in the text. This process produces the cipher text block. The ciphertext is an unreadable conversion of plain text data. Humans cannot read the AES ciphertext until they use the correct AES key to decrypt the data.
AES has three key sizes
- 128
- 192
- 256
Although the key length of the AESA encryption algorithm varies, the block size is always 128 bits. Many of you might wonder why there are different key lengths. Many of you might also question that if the 256-bit key is the strongest of the lot, then why don’t we just use this single key instead of the other two?
The thing is, there are resource constraints. For instance, if you have a mobile app that uses AES-256 instead of AES-128, then it will drain the phone’s battery faster. Hence, if your app does not require a higher level of encryption, it is best to go with a lower level of encryption to save on resources utilized.
Example of how AES encryption looks like:
Can you decipher the following ciphertext message?
bWhVOg5IxuiUw1TKrEjFD4CCw9r30KcSp8LU49JXX89i5+K/Z55QeNgPnEoDtK90bbUjpbQZ/yaQGOdXlbZS9/Ntd/mfxnK6GAhyKmtHUUk=No? Thought so. Here is the plain-text version
Plaintext message: Doctors diagnosed the acting president with a potentially terminal illness.
You can only decipher the message if you have the correct AES encryption key.
What are some Examples of AES Encryption?
Many everyday uses of the AES algorithm exist today, not just limited to Federal agencies employing it. It may surprise you to know that many solid-state drives (SSDs) already utilize the AES encryption algorithms. This ensures that the data is encrypted and protected from the moment the SSD is produced in the factory.
- Many SSD manufacturers equip their hard drives with 256-bit AES hardware-based encryption, keeping hackers out of the equation.
- Virtual private networks, or VPNs, popularly utilize the Pratik encryption standard to securely connect you with another server, typically located in another country. As VPNs have to switch between servers dynamically, they can afford to use only the best methods of encryption. Popular VPN services like NordVPN and ExpressVPN use the AES-256 bit key to secure their customers’ browsing data.
- Your social media messages are also encrypted. So that you do not need to worry about someone reading your messages and extracting critical information about you from those messages. The popular social media messaging platform WhatsApp employs the AES algorithm. WhatsApp encrypts its messages using 256-bit AES encryption. This makes it extremely difficult for hackers to hack into your WhatsApp messages.
- The world’s favorite desktop operating system, Windows, also uses AES 128-bit and 256-bit encryption.
- All data stored in Google Cloud is encrypted using a 256-bit AES encryption by default.
- LastPass is one of the most famous password management applications. LastPass uses AES encryption. The AES encryption helps LastPass to keep the user’s password safe from hackers. Even Lastpass employees cannot access the password of users.
- The US military, national security agencies, and many other US government entities use AES encryption to secure data storage.
A classic example of AES encryption in action is your internet browser. Whenever you visit a website with https in its URL, it is very likely that a TLS / SSL certificate secures it. This means that the website uses AES encryption to maintain the security and integrity of your browsing sessions. Another common use of the AES algorithm is in Wi-Fi. Wi-Fi is secured by WPA2-PSK (AES) encryption. Even Facebook Messenger uses the AES encryption standard.
Final words
The AES encryption standard has become the gold standard for encrypting sensitive data across a wide range of applications. If you are considering building an app that deals with sensitive data, then it is best to consider the security mechanism the app will have. The AES encryption standard is just one of the many robust encryption standards available. Understand that you must select the most appropriate encryption standard to ensure your app performs optimally. You can take expert opinion for this.