What is SSL Stripping and How to Stop SSL Stripping Attack?
Overview of SSL Stripping and How to Stop Stripping Attack
In today’s digital age, security is of the utmost importance when it comes to online transactions and communication. SSL (Secure Socket Layer) establishes a secure connection between web servers and browsers. However, SSL stripping still poses a potential threat even with the use of SSL. It has proven to be dangerous to cybersecurity as it allows attackers to intercept and modify SSL/TLS encrypted traffic.
Here is an SSL stripping explained in easy terms.
What is SSL Stripping?
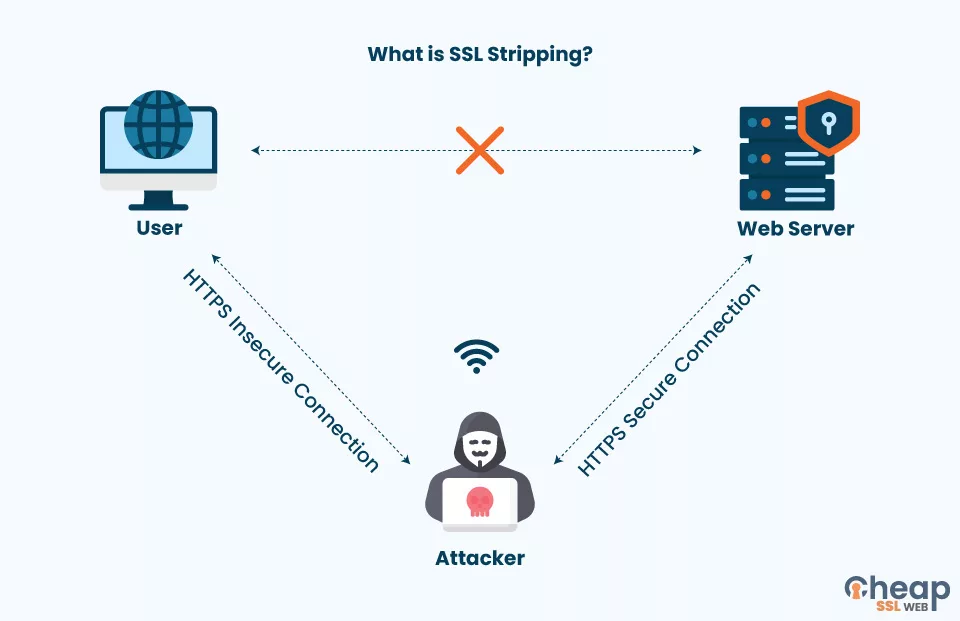
In SSL stripping, an attacker intercepts and modifies a client’s and server’s communication. This downgrades the connection from a secure HTTPS connection to an insecure HTTP connection. Thus, the attacker can view or modify the data transmitted between them. These attacks are particularly dangerous, as an attacker can intercept the communication between a client and a server in real time without the client having any knowledge about it.
An attacker can launch SSL stripping attacks through a number of methods, like using a malicious Wi-Fi hotspot or using a man-in-the-middle attack to intercept the traffic as it passes through a network.
So how does SSL stripping work? Let’s find out.
How Does SSL Stripping Work?
Let us take an example and explain this better.
Three things are required for SSL stripping to occur:
- Attacker A
- Victim B
- Server C
In an SSL stripping attack, the victim (B) may mistakenly believe that the data they are exchanging is secure and encrypted when the attacker transmits it over the network to the server. However, in reality, the attacker is able to intercept and modify the communication between the client and the server, acting as a man-in-the-middle (MiTM). As a result, the attacker can view and potentially modify the data in transit since it is not encrypted. This can expose sensitive information such as login credentials or financial data to risk and undermine the victim’s trust in the security of their communication.
This is how the SSL Stripping attack happens:
- Victim B wants to open their internet banking over a secure HTTPS connection. But at the same time, the attacker, too, wants to access B’s credentials.
- To gain access to all the confidential information of B, attacker A intervenes and modifies the communication between B and server C. Thus; the attacker cuts off the secure communication between the two.
- When victim B tries to access their banking website, attacker A acts as a default gateway and intercepts their request. After receiving all the details in an unencrypted form (as A has interrupted the secure connection), it forwards all the details to the server, thus acting as a ‘bridge’ between B and C.
Note: During this process, the connection between A and C remains secured so no third-party can intervene there, but the connection between A and B remains unencrypted.
- If attacker A is successful in stripping the SSL encryption in a man-in-the-middle (MITM) attack, any data that victim B types, including login credentials, passwords, and credit card numbers, will be transmitted in plaintext and will be vulnerable to interception and modification by the attacker. This can expose sensitive information to risk and undermine the victim’s trust in the security of their communication.
There you have it! It is that easy to get in the middle and steal user information. So what can be done? First, let us discuss the best ways of combating sslstrip. But before that, let us discuss why it is such a threat to cybersecurity.
What is the Threat of SSL Stripping Attacks?
SSL stripping is a serious threat to cybersecurity. Cybercriminals leverage it to steal sensitive data and cause significant damage to individuals and organizations. Thus, it is important to be aware of this threat.
Some of the potential risks of SSL stripping include the following:
- Phishing
- Data Loss
- Malware
- Brand Damage
- Legal Issues
Phishing
With SSL stripping, an attacker intercepts and alters the communication between a user and a website, stripping away the SSL/TLS encryption and leaving the communication unencrypted. The attacker can then trick the user into providing sensitive information on the fake login page, which can then be used to steal their identity or access their accounts.
Data Loss
With SSL stripping, communication between two servers becomes unencrypted. Thus, the attacker can easily obtain potentially stolen sensitive information, such as login credentials, personal information, financial data, and more.
Malware
An attacker can also inject malware or phishing content into the unencrypted communication, tricking the user into giving up even more information or downloading malware onto their device. The attacker can steal or manipulate the sensitive information being transmitted over the unencrypted connection, resulting in data loss.
Brand Damage
SSL stripping can damage a brand’s image by exposing users to phishing attempts and other types of cyber attacks that can compromise their personal and financial information. This can lead to a loss of trust among customers and potential customers, as they may become wary of using the brand’s website or services. This can result in a loss of business and revenue for the brand.
Legal Issues
SSL stripping can have legal repercussions because it is a form of hacking and can result in the unauthorized access or theft of sensitive information. It can also result in the unauthorized use or alteration of data, which can lead to financial losses and reputational damage for the affected organization. Most jurisdictions consider this illegal and impose severe penalties, including fines and imprisonment. Furthermore, customers or other parties whose information was compromised may take legal action against the companies affected by SSL stripping.
This is how ssl stripping can be severely serious. So how can we stop it? Let’s find out.
How to Stop SSL Stripping?
It is important to note that SSL stripping can occur in various ways, and no single solution can provide complete protection against it. Therefore, it is recommended to implement multiple solutions to increase your security level.
● Enable SSL of a Reputed Certificate Authority (CA) Sitewide for your Website
The browser displays a warning message if a website uses an SSL certificate issued by an untrusted CA. The warning message is an indication that the browser does not trust the certificate. So the users are more likely to fall victim to SSL stripping attacks. It is because many users may not be aware that the website they are visiting is not secure.
Therefore, it is important for website owners to get SSL from a reputable certificate authority (CA). Most web browsers and devices trust a reputable CA’s SSL certificate, making it difficult for attackers to intercept and strip the SSL.
● Implement HSTS Policy
The HTTP Strict Transport Security (HSTS) policy is a web security mechanism that tells browsers to only connect to those websites that use a secure HTTPS connection and never via an insecure HTTP connection. Upon the implementation of the HSTS policy, a website directs the browser to automatically redirect any HTTP requests to the HTTPS version of the website.
So when a user types in the website’s URL with ‘HTTP’ instead of ‘HTTPS,’ the browser will automatically redirect them to the secure version. This makes it much harder for an attacker to perform SSL stripping, as the browser will automatically detect and prevent any attempts to connect via an insecure HTTP connection.
● Use SSL Pinning
SSL pinning, also known as certificate or public key pinning, ensures that a website uses a trusted SSL certificate. The process involves ‘pinning’ or hard-coding the client software’s specific SSL certificate or public key.
When a web browser connects to a website, it checks the SSL certificate presented by the website against the pinned certificate or public key. The connection terminates if the certificate or key does not match, as it indicates a potential SSL stripping attack might be in progress. This helps to prevent SSL stripping. Thus, only the trusted SSL certificate is used for the website, not the one an attacker has intercepted.
● Using SSL Inspection Tools
SSL inspection tools, also known as SSL proxying or SSL decryption tools, intercept and inspect encrypted SSL/TLS traffic. These tools actively prevent SSL stripping by monitoring the network for SSL stripping attacks and actively blocking them before they can execute.
The process involves intercepting SSL/TLS traffic, decrypting it, and then re-encrypting it with a new certificate before forwarding it to the intended destination. This allows the tool to inspect the traffic for malicious activity and block it before it can cause harm. It also allows the tool to monitor the traffic for compliance with security policies and to identify and block any attempts to bypass security controls.
● Using SSL/TLS Acceleration Hardware
SSL/TLS acceleration hardware is a device specifically designed to offload the SSL/TLS encryption and decryption process from the main server. The application of the hardware frees the main server from the heavy burden of SSL/TLS encryption and decryption. This increases the overall performance of the server.
The SSL/TLS acceleration hardware also prevents SSL stripping by providing an extra layer of security. The device can be configured accordingly to inspect all SSL traffic and only allow traffic from a trusted source. With an additional layer of security, it becomes much more difficult for an attacker to perform SSL stripping, as this acceleration hardware will detect and block any attempts to intercept or modify SSL/TLS traffic.
These are some of the ways to prevent sslstrip from happening and make sure your end-users enjoy safe and hassle-free web browsing.
Concluding Words
SSL stripping is a fatal attack that targets the SSL encryption of a website, leaving it vulnerable to data breaches and phishing attempts. It undermines the website’s security and can cause serious damage to its brand image and reputation.
With the increasing rate of cyber-attacks, it is important to have a robust security system in place to keep your website and its users safe from any kind of security breaches. Implement the above-mentioned measures and say NO to cyberattacks.