What is End-to-End Encryption and How Does It Work?

With privacy and online security becoming an increasing concern in the public domain, ensuring them has become a higher priority than ever before.
However, on seeing reports such as the fact that 79% of internet users believe they have no control over their data, the world of cybersecurity may seem a little bleak.
However, it is likely that on using your favorite messaging applications, you may have come across a message saying messages and calls are end-to-end encrypted. This is displayed when the developers ensure the privacy of your conversation.
To understand how privacy and internet security are protected today, it’s essential to know the basics. Since Ancient Greek times, our best way of protecting the confidentiality of information has been encryption.
So let’s go over what it is and how it works.
What is Encryption?
Encryption is the way of scrambling up messages from a readable format (also called plaintext) to an unreadable format (also called ciphertext). This is done with the aid of a key that can encrypt (scramble) or decrypt (unscramble) the given information.
One of the most basic encryption algorithms is Caesar’s cipher which encrypts by shifting each character to the right by a certain number. This number is the key in the case of this cipher.
For example, let’s take the plaintext “Meet in the park” and key 4:
Plaintext: Meet in the park
Key: 4
Ciphertext: City Mr xli tevo
This ciphertext wouldn’t make sense to anyone without the key; therefore, the message would be secure. Modern ciphers work in a similar yet more complex manner.
Types of Encryptions: Symmetric and Asymmetric
Modern encryption methods are broadly classified into two categories – symmetric and asymmetric. The symmetric encryption method works by using a private key that is shared between the sender and the receiver. However, this method is less secure since the private key can be intercepted via a man-in-the-middle attack.
On the other hand, asymmetric encryption uses two separate keys for encrypting and decrypting the message. The public key is used for encrypting and is shared between the client and the server. The sender encrypts the message using this key, and the receiver uses their private key to decrypt it without sharing it. This method of encryption has been gaining popularity ever since the early 2000s. Modern connections such as the SSL protocol utilize asymmetric encryption algorithms to prevent most intercepting attacks.
The Transport Layer Security (TLS) Protocol
The Transport Layer Security Protocol or TLS Protocol is an advanced version of the SSL Protocol. It has better security features and patches vulnerabilities frequently in updated versions. In fact, the famous “HTTPS ” that you see in domain names of secure websites is implemented by the TLS Protocol.
The TLS Protocol is very secure, and it utilizes some of the best encryption algorithms, such as the RSA algorithm, in its encryption processes. As a result, it is used by most businesses across the world, including banks, to preserve the integrity and confidentiality of their data.
Unfortunately, the protocol isn’t very helpful in the case of direct communication between users since it doesn’t support such connections. As a result, in order to use TLS, your data would still have to be shared with a third party before being sent to the end-user. If the third party is attacked, it leaves your data vulnerable as well.
End-to-End Encryption: A New Dawn of Privacy
The solution to the above problem comes in the form of end-to-end encryption or E2EE. This encrypts the communications between both the sender and receiver directly and prevents any third parties from accessing the encrypted message. Moreover, the message is only decrypted at the recipient’s device.
This form of encryption is made especially for mobile devices and instant messaging. It works with asymmetric encryption where the private keys are only stored on the devices of communicating parties.
In comparison with communication methods such as email, it is much harder for attackers or spying third parties to intercept the communication. In the case of email, it would be easy for the attackers to hack the servers or even attack the browser of the user to intercept the communication.
Even if the attackers are able to hack into the servers in the case of E2EE, they would only be able to access encrypted messages with no way of decrypting them. This would make the hacking attempt unfruitful and still safeguard the privacy of the communicating users.
Where is End-to-End Encryption Used?
Today, end-to-end encryption is most famously used in messaging applications by Mark Zuckerberg’s Meta. WhatsApp was one of the first messaging applications to incorporate the system. However, now all three of the company’s messaging applications – WhatsApp, Facebook Messenger, and Instagram have started using it.
What Known Vulnerabilities Exist for End-to-End Encryption?
No system is 100% foolproof, as weak links always exist. While in the case of E2EE, the attackers cannot access encrypted messages from the servers. They can still do so by accessing one of the user’s devices.
E2EE prevents any chance of phishing for the most part since it is mostly device locked. However, it is possible to install spyware that can receive decrypted messages at the device level. Despite this, E2EE is still the most secure form of communication to date, and these vulnerabilities do not directly impact it.
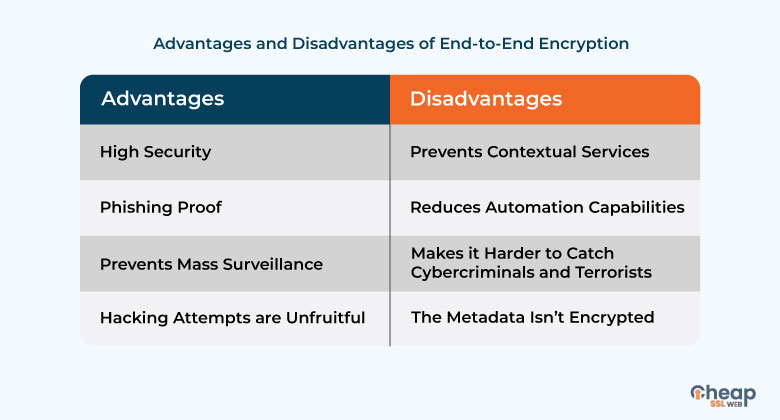
Benefits and Disadvantages of End-to-End Encryption
End-to-end encryption is one of the security technologies that have been publicly opposed by government officials on a global scale. The primary reason is that it prevents possibilities of mass surveillance as the servers are always encrypted. However, there are others who have spoken against the use of E2EE over the years. The primary advantages and disadvantages of the service are:
Final Thoughts
Using an end-to-end encrypted messenger can make you feel a lot more secure while talking online. Your communication data will not be shared with any third party and will remain encrypted until it reaches the recipient. While this comes with several benefits, it does have a few disadvantages as well, and it is up to you to decide whether to use it or not.
Read also about What is Spyware? Examples of Spyware Types Explained