What is a Certificate Authority (CA) in PKI? How Does Certificate Authority Work?
What is a Certificate Authority (CA)?
A Certificate Authority (CA) is an organization that provides digital SSL/TLS Certificates to entities that deal with collecting and storing user data. These entities verify the information provided by the organization claiming to be who they are.
Introduced in 1995 by Netscape, SSL/TLS certificate is a technology that encrypts information transmitted between a user and server. In Layman’s terms, these certificates turn sensitive information into an undecipherable format so that a cyber-attacker cannot read or tamper with it.
As you may concur, the certificate authorities provide digital certificates. Web browsers and the CA/Browser Forum publicly trust these organizations. In addition, CAs verify the identity of the website’s owner to make sure they are who they claim to be.
What does a Certificate Authority Do?
There are two important activities that CA does:
- Vetting (verifying) the identity of the website owner or organization: When you request a certificate from CA, it verifies the information you provide. This information includes the organization’s name, domain name, address, email address and a public key.
- Issuing the certificate: Once the CA validates the information, it issues the certificate in the organization’s or domain’s name.
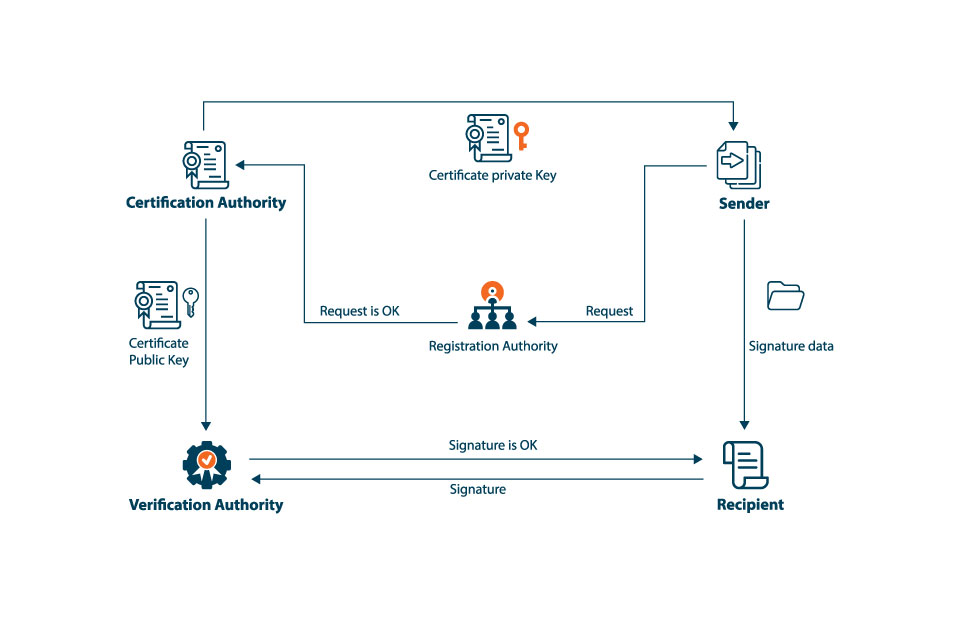
How Does Certificate Authority Work?
Once the CA issues the certificate for the website, users can trust the website with their data.
SSL Certificate Chain Of Trust
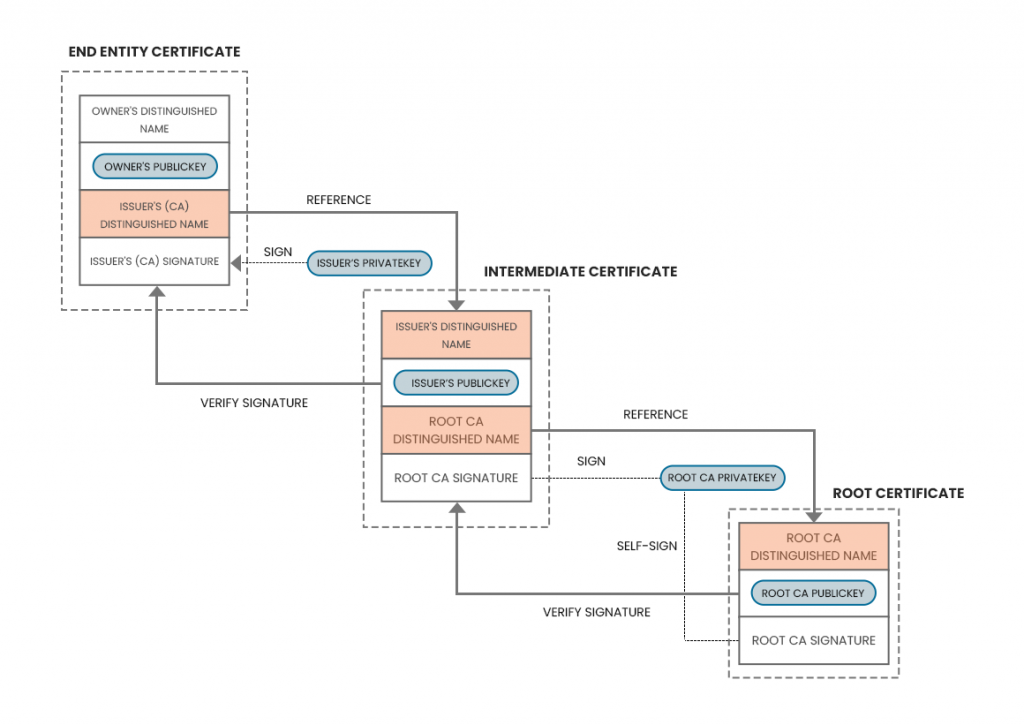
- The chain of trust is the hierarchical structure of digital certificates in which the originating entity is the root certificate (the certification authority itself)
- Next up is an intermediate certificate that insulates the CA certificate and the end-entity, i.e., the website.
- Finally, the end-entity certificates validate the website’s, owner’s, or person’s identity.
What are the CA Certificates?
If you have a passport, you know how ready you must be to prove who you are!
You are asked about your birth and your residence. You have to give the proof to prove you are telling the truth. The passport tells the entire world that you are who you claim to be.
Getting a digital certificate or, say, the CA certificate is a purely online process, and you need to provide the information you asked about the company for which you are requesting the CA certificate. It is the web passport for your website, and it contains the information and the encryption key that tells the users that they have made a secured connection with the website. It keeps the data safe from man-in-the-middle (MiTM) attacks.
The Importance of Certificate Authorities in PKI
Certificate Authority is the cornerstone of a larger Public Key Infrastructure (PKI) system. The below image shows the important parts of PKI.

The important aspect of digital security is that the third person should not be able to access the information stored on the servers. The information has to be between the user and the website itself. It asks the websites to update their security to get the SSL/TSL certificates.
The certificate authorities are not only responsible for making sure the websites are secured but are also responsible for revoking the certificate if any malicious activity is detected. In simple words, these authorities’ objective is to ensure that the internet stays a safe place for both website owners and users.
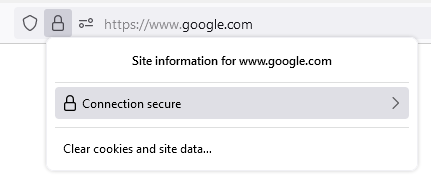
In the above image, there’s a padlock visible on the left of the URL. This padlock is an initial cue that tells the user that the website is safe to use.
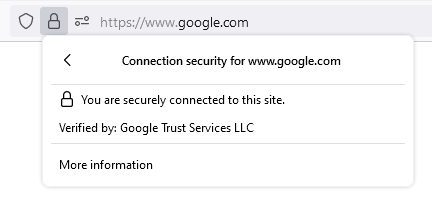
When the user clicks on the padlock, they can see a tab pop up. The tab shows that the connection is secure. When the user clicks on “Connection is secure,” they land on the tab shown in the image on the right.
The image on the right shows the text “Your information (for example, passwords or credit card numbers) is private when it is sent to this site,” which proves that a CA-approved SSL certificate secures the website.
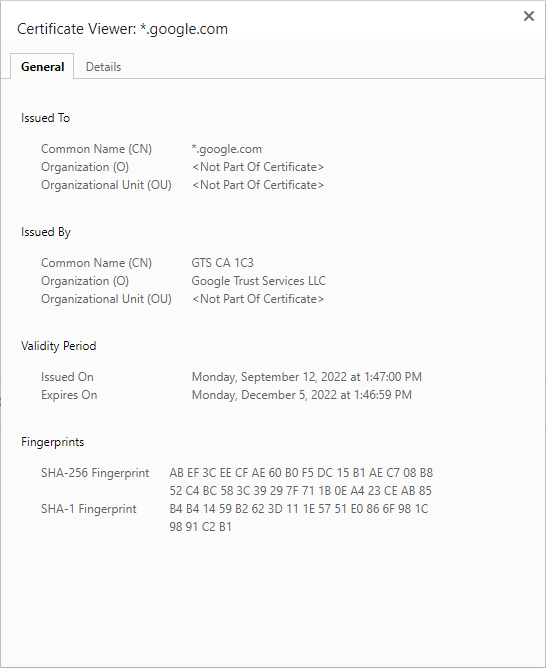
Upon clicking on “Certification is valid,” a new window appears that shows the certified information from the certification authority. It contains information such as the domain name to which the certificate is provided.
The certification authority that has provided the certificate. In this case, it is DigiCert Inc. This information also contains the date from and through which the certificate stays valid.
When does the CA Certificate Get Revoked?
- If the certification authority realizes it has improperly issued a certificate, it revokes the certificate and issues a new one for the same entity.
- If the CA discovers that the certificate used by an entity is a counterfeit, it revokes the certificate and adds it to the Certificate Revocation List (CRL).
Note: The certificate is not added to the CRL if it has EXPIRED.
Other reasons your certificate might get revoked for:
- The CA that provided you with the certificate has been compromised.
- The domain you get the certificate issued for is no longer under your ownership.
- The operations of your entity are ceased entirely.
- On the replacement of the old certificate with a new certificate.
Revocation of certificates isn’t uncommon and happens every now and then. In 2019 Google and Apple revoked not thousands but millions of certificates due to the mistaken issuance of non-compliant 63-bit serial numbers.
Public CA vs. Private CA Comparison
| Public CA (Certificate Authority | Private CA (Certificate Authority |
|---|---|
| Public CAs are the certification authorities trusted publicly by the users. | Large organizations do the major use of Private CA for their internal purposes. |
| Issues the majority of Certificates on the internet. | One needs a Public CA to provide services and showcase products to mass audiences. |
| Favorable in scenarios where a limited number of certificates need to be issued. | Organizations have multiple domains and departments. So, the Private CA is used in order to create a large number of certificates |
| For transparent communication over the internet. | For the internal operations of an organization. |
For Example – Sectigo Comodo Digicert Entrust Datacard GlobalSignGoDaddy Let’s Encrypt | For intra-communication and maintenance of data within the company’s departments. |
For Example – Sectigo Comodo Digicert Entrust Datacard Globalsign GoDaddy Let’s Encrypt | For Example – Virtual Private Networks (VPNs) Internet Sites Private E-mail Signing Certificates Closed User-Group Services File Sharing Applications |
Certification Authority List and Who Certifies the Certifiers?
From the table we just saw, we understood that different certificate authorities provide the certificates after validating the information received from the website owners.
The List of Popular CAs
Listed below are the most popular CAs from the handful that is available
- Sectigo SSL
- Comodo SSL
- DigiCert
- Symantec
- RapidSSL
- GeoTrust
- Thawte
- Network Solutions SSL
- GoDaddy SSL
- Entrust Datacard
Different larger entities approve this certificate authority List.
This lands us on one question! Who decides which authorities are to be publicly trusted?
Well, it’s a very excellent point to cross your mind!
- Microsoft decides the CAs to be trusted publicly by Windows Machines
- Apple decides the CAs to be trusted publicly on their devices and the Safari Browser
- Mozilla decides the CAs to be trusted publicly in Firefox and Linux Machines
How CAs Help Take Control Over Cyber Crime & Maintain Peace in the Virtual World
We access so many websites and so much data through the internet every single day. The internet happily serves everything on a platter with more than you need.
The CAs are responsible for making the internet a safer place for users and organizations – validating the individuals and organizations – issuing the certificates for authentication, and facilitating encryption. As breaches continue to find a way to commit cybercrime, getting an SSL/TLS certificate isn’t optional now. We hope this article was helpful to you in understanding what certificate authority is.
