What is SSL Pinning & How Does It Work? [An Ultimate Guide]
SSL or Security Socket Layer is a technique, or we can also call it an arrangement to secure communication between two entities. When two devices connect, the sender and receiver must ensure that no third party can listen to or access their communication. SSL pinning is one of the ways to ensure this.
Today, SSL pinning has become necessary in the wake of increasing unauthorized access attempts and hacks. There have been instances where website owners have received fake SSL certificates. These fake certificates present the same risk as not having SSL protection.
In this blog, we will talk about SSL certificate pinning in detail and address the current issues and solutions.
What is SSL?
Security Socket Layer or Transport Layer Security are two ways to ensure encryption in communication. Websites or online platforms that secure their data with SSL receive the designation of HTTPS before the URL address.
A key aspect of SSL is the “Chain of Trust”. This means a trusted Certificate Authority (CA) provides the SSL certificate to a website. A significant reason for the implementation of this system is to prevent Man in the Middle Attack (MITM).
These attacks try to find a vulnerability in the communication’s security system and exploit it to gain access. The attackers might also have malicious intentions, which is risky to both the sender and receiver.
In the mobile and internet banking era, it is essential to implement the perfect security system to protect everyone from hacks and attacks.
Despite these measures, risks persist as several organizations have been caught issuing malicious and fake SSL certificates. The hacker would pose as a certificate issuance authority and gain access to the internal systems of the involved parties.
SSL pinning is partly related to establishing a protective layer and partly to the mis-issuance of the SSL certificates, which will put the data on the website and the customer’s information at risk of access.
What is SSL Pinning?
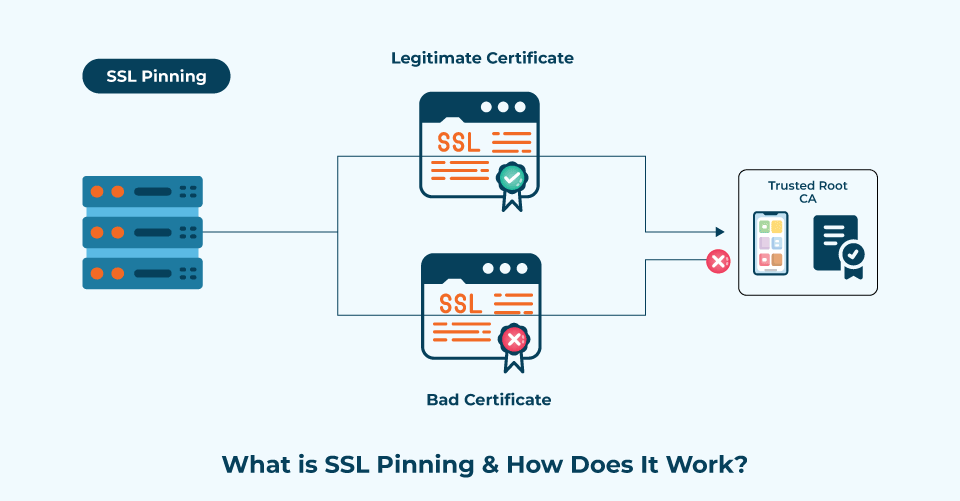
SSL Certificate Pinning is one technique utilized to prevent unauthorized access and enhance website security. The SSL or TLS certificate pinning leverages cryptographic security to identify and prove the identity of the server or host.
Under this, we can pin the identity of a secure and trusted trustworthy certificate. Consequently, the system blocks any document or attempt to access it, particularly those originating from a suspicious server.
Websites and platforms enabled with SSL pinning have a repository of stored certificates. They do not rely on certificate stores to establish the security of the same. With this, the users can create and save a list of trusted SSL certificate issuers to the application or website.
It will check and compare the server certificates from the list while establishing communication. If the system deems the connection trustworthy, it establishes it. Alternatively, users will receive a warning message or will be denied access to the platform.
SSL pinning is like double-checking the connection. Once the usual mechanism verifies it, the second checkpoint involves the pinning process. SSL certificate pinning ensures that even when a website owner or an application has installed a malicious or fake certificate, it won’t allow the users to establish a connection.
What is the Chain of Trust?
The Chain of Trust represents the hierarchy of the certificate issue, which goes back to three tiers. The first tier is the issuance of the certificate by the server. For instance, if someone wants to build a web application and wants to add an SSL certificate to it.
The server will send the certificate’s public key to the user, and the frontend code will register it. A Certification Authority (CA) signs this certificate, with the Root Certificate being the signer of the third tier. The Root Certificate is self-signed.
What are Digital Certificates that Secure the Connection?
Where SSL is a technique, the document ensuring its implementation is a certificate. The certificate holds all the information about the server for which it is issued.
Consider it as an identification card. The websites and applications that have this sort of ID are safe and will protect their user’s information. Imagine an application without an SSL certificate.
Any third party can access the bank records of individuals and customers using the application. The bank’s servers store everything, including account passwords and credit and debit card information.
The SSL digital certificates use an X.509 standard, defined by the International Telecommunication Union. A CA can also issue digital certificates, but that is where the trouble can arise.
A digital certificate holds the following information;
- Subject: The recipient is the recipient to whom the certificate is issued. It can be a user, network device, computer, platform, etc.
- Serial Number: It’s a unique number assigned to each certificate.
- Issuer: The issuing entity, usually the CAs, is named in this column with a unique name.
- Validity: The system writes the certificate’s Valid From and Valid To dates. Once the Valid To date is reached, the certificate is deemed invalid.
- Public Key: In encryption, there is a public key that will grant access to the users. This certificate holds the public key that will help establish a secure connection
- Algorithm Identifier: As every certificate signs the deal for two entities to establish a secure connection, Algorithm Identifier tells the name of this algorithm used here.
- Version: Notifies about the certificate version.
- Time Stamp: Shows the date and time of the certificate creation.
Protection Provided by SSL Certificate Pinning
We have talked about what pinning is and its certification. Moving on, let’s get to know something about this mechanism and its protective cover. We have already talked about the mis-issuance of certificates. This significant anomaly in the system is utilized to exploit server connections.
Mis-issuance occurs when a fake certificate is wrongly attributed to indicate that a domain, host, or computer is protected when, in fact, it is vulnerable. Hackers are not only after the domains and hosts but also attack the Certification Authority and start issuing fake certificates.
Due to this, they will get access to the CA’s records and to the records of the subjects. Pinning protects all types of senders and receivers. Once a certificate is issued, the user’s browser or device compares the pinned data and attempts to find any mismatches.
If a mismatch occurs, the system will send the users a warning message and notification. Additionally, the system may block users from accessing the website or application entirely.
How Does the SSL Certificate Pinning Work?
Remember the Root Certificate we talked about earlier? We can only put a limited amount of trust in the SSL certificates, especially in the authorizing entities.
In other words, the server that has sent the certificate, signed by a CA, may not have the luxury of our trust. And neither does the Root certificate. So how do we resolve this issue?
One way to resolve this issue is by loading the Root Certificate into the device. It can be a mobile or other platform used here. And we assign random names to these certificates. It can be Root 1, Root 2, and so on and so forth. These self-signed root certificates gain global acceptance and trust.
Now imagine that a hacker issues the same certificate by slightly changing the name. For instance, if someone issues the original certificate in the name of g.com, they may issue the fake one as gs.com. And this is how the MITM attacks can take place.
The person attempting to establish a secure connection with the server will see that they are going to g.com. But they are going to gs.com, and the user’s device or browser will trust, even the fake certificate.
Certificate pinning works to ensure that whatever you read above doesn’t happen. SSL pinning comes to the rescue by hardcoding the said certificate into the device.
Above, you must have read about encoding the public key into the client device. But we can also pin the certificate by encoding it, the CA, or the Root Certificate.
Now we can also hash it to the device and ensure that the client always accesses the right server with complete encryption. Post this: The connection establishes only when the certificate matches the pinned data.
SSL pinning works exceptionally well in preventing MITM attacks. It also works well with DNS Poisoning-based attacks.
Hash Key Pinning or Pinning with Public Key
In the above scenario, updating the key is necessary every time the certificate is updated to ensure a stable connection. However, we can use a hash key to avoid updating it every time and still ensure a secure connection.
With hashing, even after the certificate updates or changes, the underlying public key associated with the certificate will be able to establish secure communication. This helps us make a more dynamic and flexible pinning system, one which is conducive to the present-day system. Implementing the hash key system can be a bit challenging, but it is achievable. So essentially, we are not storing the public key itself but only recording its value, preferably in the form of SHA 256, and storing it in the system.
Pros of SSL Certificate Pinning
- SSL Pinning provides us with better and tighter security.
- It protects the clients and servers from establishing an unsafe connection due to certificate mis-issuance.
- With SSL pinning, there won’t be any eavesdropping and exposure to device malware.
- It instantly detects and reports MITM attacks.
- SSL pinning provides some level of protection from DNS poisoning attacks.
Cons of SSL Certificate Pinning
- Without hashing, changing the certificate and public key becomes a nuisance.
- With the SSL certificate pinning integrated into an application, it is difficult to insert additional security solutions.
Conclusion of What is SSL Pinning
The entire internet is rooting for users to build connections and the SSL technology is here to uphold every individual’s privacy rights and freedom. There are still threats to creating a secure communication channel, which is why we use SSL pinning. The SSL certificate pinning might be a complex process to implement, but it is an essential step toward building a highly secure communication channel.
