How to Send An Encrypted Email from Outlook

A Step-by-Step Instructions on How to Send an Encrypted Email from Outlook
Email is the most popular method for businesses to interact with clients and suppliers on the outside. Every day, we send countless emails as we send contracts, invoices, and other crucial business papers across the globe. Email security is the only issue.
Encrypting emails jumbles their contents, making them accessible only to the intended receiver. In this blog post, we’ll go through how encryption functions, why it’s significant, and the simplest ways for businesses to use email encryption. Let’s get started!
Steps to Send An Encrypted Email from Outlook
The protocol used to secure email communication is S/MIME (Secure/Multipurpose Internet Mail Extensions). It uses digital email certificates to provide authentication and encryption, ensuring that the email is only accessible to the intended recipient.
Let’s discuss the steps on how to use an S/MIME certificate to send and receive encrypted email.
Step 1: Obtain an S/MIME Certificate
The first step to using S/MIME to send and receive encrypted email is to obtain an S/MIME certificate. You can obtain an S/MIME certificate from a trusted third-party provider like Comodo, or Sectigo. You will need to provide personal identification information, like your name and email address, to get the certificate.
Step 2: Install the S/MIME Certificate
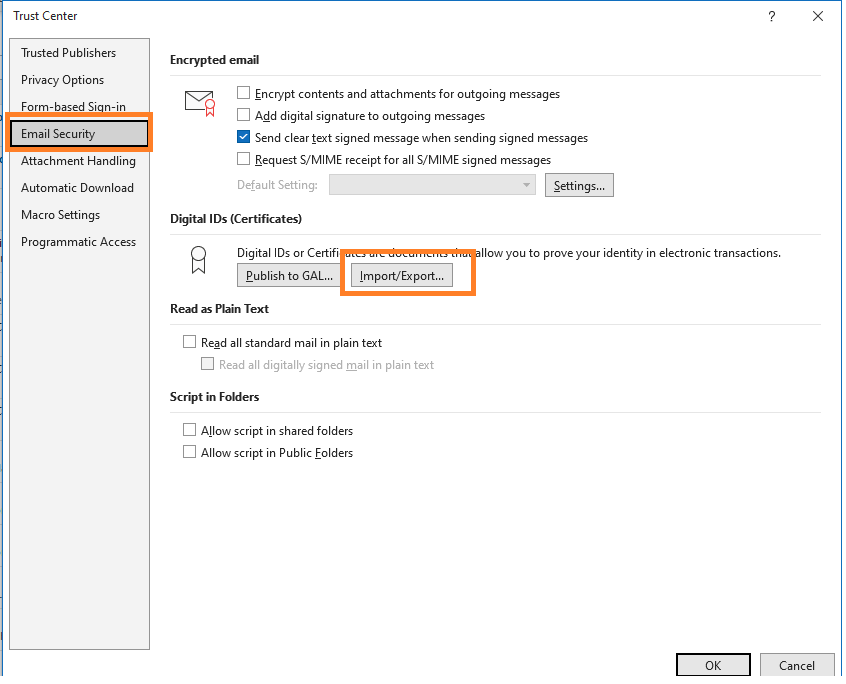
Once you have obtained the S/MIME certificate, you need to install it in your email client. The process for installing the certificate varies depending on the email client you are using. For example, in Outlook, you can go to File > Options > Trust Center > Trust Center Settings > Email Security > Import/Export to install the certificate.
Step 3: Configure Email Client for S/MIME
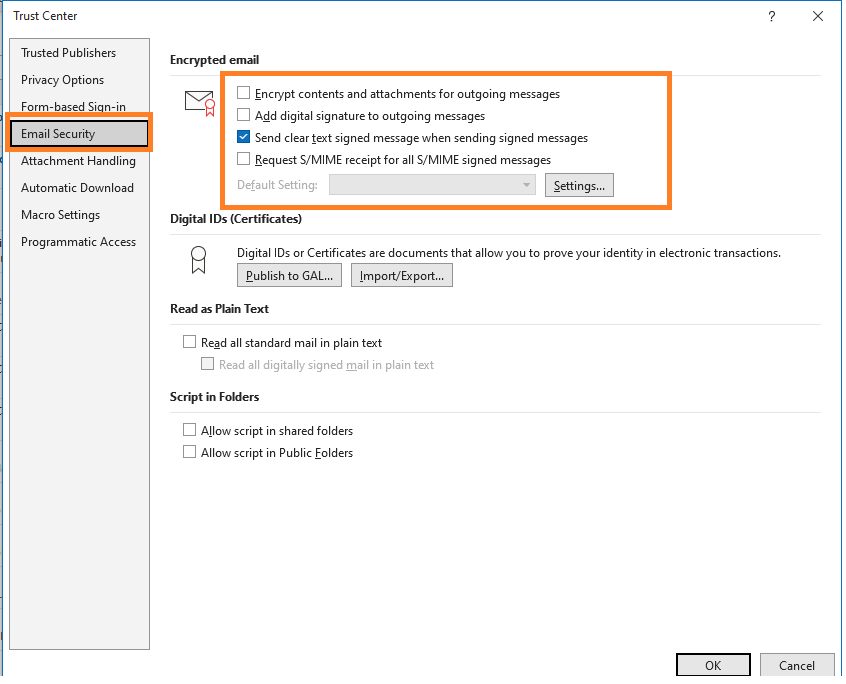
After installing the S/MIME certificate, you need to configure your email client to use S/MIME. In Outlook, you can go to File > Options > Trust Center > Trust Center Settings > Email Security to configure S/MIME settings. You can select the certificates to use for signing and encrypting emails and set other security options.
Step 4: Send Encrypted Email
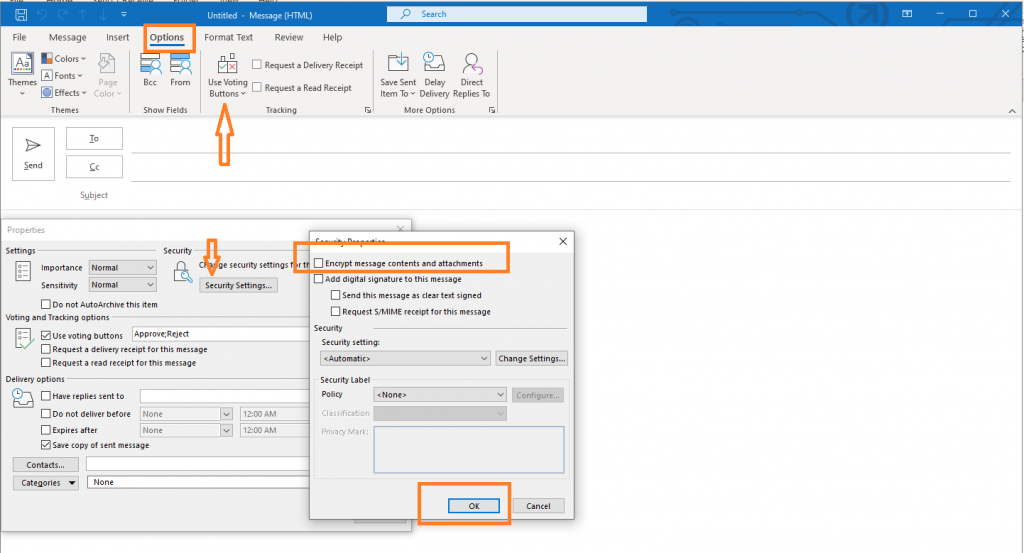
To send an encrypted email using S/MIME, compose a new email and click on the “Options” tab. Click on “Encrypt” to encrypt the email. The recipient needs to have an S/MIME certificate installed in their email client to decrypt the email.
Step 5: Receive Encrypted Email
To receive encrypted email using S/MIME, the sender needs to have your S/MIME certificate installed in their email client. When the sender sends you an encrypted email, you will receive a message that the email is encrypted. You will need to have your S/MIME certificate installed in your email client to decrypt the email.
What is Email Encryption?
Email encryption is a type of authentication that prevents unauthorized or unintended persons from reading messages. The original communication is transformed into an unintelligible or unreadable format. Encryption is necessary when sending sensitive material over email.
Hackers contact victims via email and steal data, including personal information like names, addresses, and login passwords, to perpetrate crimes like identity theft and fraud.
Most sent emails are encrypted during transmission; however, the data is retained in clear text, allowing email providers to access the content. Well-known free email providers not offering End-to-End encryption make it easy for hackers to intercept delivered communications.
Email encryption systems use public-key cryptography and digital signature technologies to encrypt email communications. By following this procedure, you may be confident that only the intended recipient will be able to open your emails.
What Does Email Encryption Do?
You can utilize encryption when sending emails containing sensitive information. When an email is encrypted, plain text is turned into ciphertext that has been scrambled. The receiver who holds the private key that decodes the email will be the only one subsequently able to read it.
Email Encryption Architecture
Instead of using a standard architecture, email encryption solutions rely on gateway software to implement policy-based encryption. Businesses may specify which emails require encryption and the circumstances under which they should be encrypted through policy establishment.
For instance, businesses frequently mandate that any user who sends an email communication containing personally identifiable information (PII), financial information, or other sensitive information must encrypt it.
Some email encryption software takes the shape of a client that users install on their desktops, laptops, or portable electronic devices.
This service can allow customers to select which emails to encrypt, utilize policy-based encryption to secure specific email messages or do both at once.
Instead of the email gateway, which guards against possible security risks on local networks, other email encryption solutions can put more emphasis on securing the machine.
However, installing email encryption software on a user’s laptop is becoming less and less necessary. They now have access to web-based interfaces that can read and decrypt encrypted messages.
Either the firm will privately host these email encryption solutions or, more typically, an email encryption software provider will offer a cloud-based service.
Methods of Email Encryption
You can benefit from encrypted PDFs and web portal encryption in addition to using S/MIME and TLS to encrypt email.
Encrypted PDF
You may provide consumers with protected documents and attachments that they can download to their computers using an encrypted PDF, zip, or Office file.
What use does email encryption serve here? Anyone attempting to intercept and use the information in the email would only receive a random collection of characters as a result.
This indicates that all attachments and documents are readable on all devices and arrive at their destinations unharmed. The user can access the attachment later while offline because they downloaded it.
Web Portal Encryption
The receiver must visit a web page to read an email that has been encrypted via a web gateway. Because the shared key protects the email before sending it to the web portal, this satisfies the definition of email encryption.
The user’s email program, such as Outlook, Mailbird, etc., sends the encrypted email directly to the online site. This prevents anyone without the website’s login information from reading the email.
This type of secure email encryption solution reduces your attack surface by reducing the number of persons who have access to your company’s emails.
Web portal encryption is a reliable means to stop hackers from accessing critical information sent over the internet, provided that the recipient’s password is safe.
Types of Email Encryption
Email encryption software usually uses three different encryption formats. These consist of the subsequent email encryption varieties:
Pretty Good Privacy (PGP)
PGP is a security tool that uses file encryption and digital signatures to encrypt and decode email communications. In 1991, the launch of one of the earliest free, widely accessible public-key cryptography programs took place.
Today, individuals and companies frequently use PGP to safeguard their internet communication, such as email and text messaging by offering cryptographic authentication and privacy.
PGP combines cryptography, data compression, symmetric and asymmetric key technologies, and various hashing methods to encrypt data in motion.
Additionally, it presents a viewpoint on the public key infrastructure (PKI) strategy. PGP encrypts the information when a user sends a message using their public key and decrypts it when the receiver unlocks it using their private key.
Secure Multipurpose Internet Mail Extension (S/MIME)
The Internet Engineering Task Force (IETF) developed the S/MIME standard to deliver public-key encryption and digital signatures.
Most contemporary email software systems now include it, which RSA Data Security created. S/MIME offers PGP-like capabilities, but it necessitates that users receive keys directly from a particular Certificate Authority (CA).
Transport Layer Security
The encryption protocol TLS (SSL) replaced the secure sockets layer. The initial introduction of TLS was in 1999, and it was based on the original SSL standards, which also made it an IETF standard.
It frequently facilitates secure messaging across computer networks, including email, voice over IP, and instant messaging (VoIP).
Data privacy and integrity between computer application communications are goals of TLS. It includes the TLS record and TLS handshake protocols and operates at the application layer.
STARTTLS, a command that transforms plaintext messages into safe, encrypted communications, is a popular variant of TLS. STARTTLS encrypts emails while they are being sent and received, meaning neither party needs to take action to access the content.
This strategy might leave businesses vulnerable to additional threats like man-in-the-middle (MITM) assaults even while it is great for thwarting attack routes like passive monitoring.
Enterprise Email Encryption: How It Protects Your Organization
Since email is not normally protected by default by protocols like TLS, messages can be sent in plaintext if email encryption is not used.
This makes email transmissions from the sender to the recipient—including the messages’ content and attachments—vulnerable to interception, reading, and theft, which is especially important when users communicate sensitive information over unencrypted email.
Additionally, a hacker can install malware on a user’s computer, giving them the ability to intercept subsequent communications and steal additional sensitive data from business networks.
Therefore, businesses must conduct an email risk assessment and implement corporate email encryption to protect all incoming and outgoing email traffic.
Users may then encrypt each message they send, or at the very least any emails that contain sensitive data or attachments, and receivers can then decode the communications they receive.
Because managing cryptographic keys may be complex, email encryption has historically been challenging for end users. However, users may now send encrypted email without time-consuming training procedures since it is much simpler to comprehend how to do so.
Who Should Use Email Encryption?
Solutions for email encryption are excellent for businesses with in-house email servers. Sending unsecured email communications puts any company that transfers sensitive data at a high risk of a cyberattack or data breach.
Therefore, it is significantly more cost-effective to pay for an email encryption service to safeguard email than to risk the possible financial and reputational harm brought on by a breach.
Organizations that handle extremely sensitive data must use the finest email encryption or are subject to strict regulatory compliance criteria to safeguard their incoming and outgoing communications.
Read also about What to Do With Suspicious Emails & How to Report It?
FAQs
What is email encryption?
Email encryption is a form of authentication that prevents unauthorized or unintended individuals from reading messages.
How does encrypted email work?
Email encryption services convert plaintext emails into scrambled ciphertext. Through public-key infrastructure, even if a cybercriminal can intercept communication and read it, they will not be able to do so.
How do I encrypt an enterprise email?
Organizations require enterprise email encryption to safeguard all incoming and outgoing email communication. This requires doing an email risk assessment.
What types of email encryption can be used?
Three different encryption formats are usually used by email encryption software. These consist of the subsequent email encryption varieties:
- Pretty Good Privacy (PGP)
- Secure Multipurpose internet mail extension (S/MIME)
- Transport Layer Security (TLS)