How to Fix the SSL Handshake Failed Error?

Fix the SSL Handshake Failed Error Code 525 in these Easy Ways
For cybersecurity, SSL-enabled websites are important; for that, SSL Handshake plays a key role. The SSL Handshake establishes a secure connection between a web client and a web server to protect sensitive information from malicious actors intercepting or tampering with it. However, users might encounter an SSL handshake failed error message during this process.
To understand the SSL handshake fail error message, it is important to thoroughly examine the SSL handshake process.
What is an SSL Handshake?
SSL Handshake is a process that involves three important functions- algorithm agreement, certificate exchange, and the exchange of cryptographic keys with the help of a shared algorithm. The server and client agree on one of the two shared algorithms and exchange cryptographic keys using an SSL certificate to encrypt client-server communication in the process.
It also authenticates the server by checking the SSL certificates. Thus, it helps in ensuring that the client is a server and not an imposter. However, often, a glitch happens during this handshake, resulting in an ‘SSL handshake failed‘ error message.
Let us discuss the error message in a detailed manner.
What is the ‘SSL Handshake Failed’ Error Message?
An error message comes up when a client or server cannot establish a secure convention. It is called the SSL Handshake Failed. It can happen due to multiple reasons- sometimes due to some issue at the client’s end and sometimes from the server’s end.
The SSL/TLS handshake failed error message might come up due to different reasons based on the client application users are using or the server they are trying to connect with. For example, an error in GitHub looks like this:
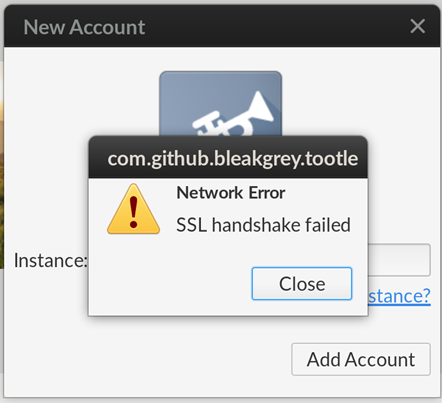
However, an error on Cloudflare will look something like this:
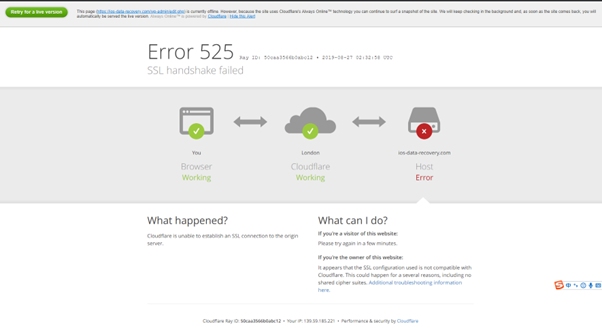
So what are the reasons that result in the error? Let’s find out.
What Causes the ‘SSL Handshake Failed’ Error Code 525?
There are multiple reasons why SSL Handshake doesn’t occurs. Here are some of the most common ones:
● The Local Device has the Wrong Date or Time
One of the steps in the SSL/TLS Handshake process is for the browser to verify the validity of the SSL certificate. To check the certificate’s validity period, a web browser or a web server needs to define the “valid from” and “valid until” fields in the certificate. If the date and time on the device are incorrect, the browser may incorrectly determine that the certificate is not valid, causing the SSL/TLS Handshake to fail.
It is because the client cannot verify the validity of the certificate. The validity period of the certificate enables its use.
The certificate has a validity period during which it can be used. If the purchased SSL certificate is expired or not yet valid, the client will reject it. Thus, SSL Handshake will fail.
The issuing certificate authority (CA) creates and signs a timestamp contained in an SSL certificate. If the date and time on the client device are incorrect, it will not match the timestamp, causing the SSL Handshake to fail.
● The Browser doesn’t Support the Latest SSL Protocol
An SSL handshake fail error message occurs when the browser and server cannot negotiate a common SSL protocol. If the latest SSL protocol is not supported by the browser, and the server only allows connections using the latest protocol, it can cause this issue. In this scenario, the browser cannot establish a connection, and displays the error message.
The error message can also pop up if the SSL certificate is invalid or not trusted by the mains server or if there is a problem with the SSL/TLS configuration on the server.
- Your SSL Certificate is Invalid
Before establishing a secure, encrypted connection, the central server verifies the SSL certificate.
If it does not recognize the certificate as valid, it will not establish a secure connection with the server. For example, A self-signed certificate will not be trusted because it is not signed by a trusted certificate authority. A secure connection cannot be established if the certificate has expired.
- Issue with the Server Name Identification (SNI) Configuration
SNI is an SSL protocol extension that allows a web server to host multiple SSL-enabled websites with different domain names on the same IP address. When the Browser sends the requested domain name during the Handshake process, the server uses this information to select the correct SSL certificate to present to the Browser.
Improper configuration of the server to use SNI may prevent it from matching the requested domain name to the correct SSL/TLS certificate, resulting in a failed SSL handshake.
If the web browser does not support SNI, the SSL Handshake may fail even if the server is configured to use it.
● Issue with Content Delivery Network (CDN)
A CDN is a system of distributed servers that deliver web content to a user based on their geographic location.
So when a user tries to access a website via a CDN, the handshake process takes place between the edge server of the CDN and the user’s Browser. If there is an issue with the CDN’s SSL configuration, the SSL Handshake will fail, and the user will see an SSL Handshake error message. The issue could arise due to an incorrect certificate, an incorrect SSL certificate chain, or a certificate that the browser does not trust.
If we don’t configure the CDN correctly to forward the Handshake to the origin server, it will show an error message.
These are some of the common reasons why SSL/TLS handshake failed error messages come up. Let us discuss how to fix it.
How to Fix the ‘SSL Handshake Failed’ Error?
You can fix the SSL Handshake Error by employing different ways. Here are some of them.
● Update Your System Date and Time
Correcting the date and time on a device could fix an SSL Handshake error if the error is related to the certificate validation process, specifically if the browser is incorrectly determining that the certificate is not valid due to incorrect date and time. While this solution may not guarantee a fix, investigators should also examine other causes of the error.
● Check if the SSL Certificate Is Valid, Configure the Browser for the Latest SSL Protocol Support
Checking if your SSL certificate is valid and configuring your browser for the latest SSL protocol support can fix an SSL Handshake error and establish a secure connection with the server. However, the error must be related to the certificate validation process or the SSL protocol version.
● Ensure that your server properly configures to support SNI
You need to make sure that your server is properly config to support SNI. The SNI configuration involves some major issues such as incorrect SNI configuration, missing SNI configuration, or missing domain name in the SNI configuration. You also have to check that both your client server and central server support SNI as sometimes the latter do not support it.
● Fixing Protocol Mismatch
Web server administrator can fix the protocol mismatch by configuring the web server and the client server to use the same SSL protocol. It allows them to establish a secure connection. Web server admin can config the browser to support the latest SSL protocol or configuring the server to support older SSL protocols that it supports.
Check that your CDN or load balancer forwards the SSL protocol version that your browser and server agree on.
These are some of the ways you can fix the SSL/TLS handshake failed error message.
Conclusion
As SSL Handshake plays a key role in keeping data in transit secure, users must understand what the SSL Handshake fail error means and how to fix it. By following the fixes we have mentioned, you should be able to resolve the issue and establish a secure connection.
