Multi-factor Authentication (MFA) Vs. Two-factor Authentication (2FA): Understanding the Key Technical Differences
The Differences Between Multi-factor Authentication (MFA) Vs. Two-factor Authentication (2FA) Explained
To make your website difficult to breach, you need additional layers of security, and identity authentication can save your day. Although people use two-factor authentication (2FA) and multi-factor authentication (MFA) interchangeably, they are different. To understand Multi-factor Authentication (MFA) vs. Two-factor Authentication (2FA), it is important to decode what is what and then see how they differ from each other.
So before we discuss Two-factor authentication (2FA) and multi-factor authentication (MFA), Let us start with 2FA.
What is 2-Factor Authentication?
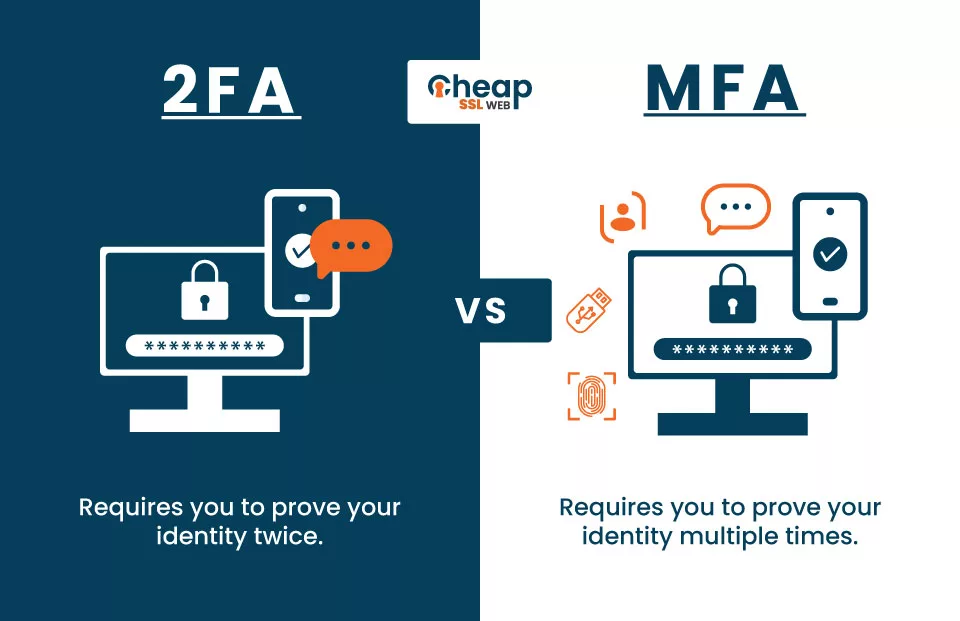
Two-factor authentication (2FA) is a security measure that requires a user to provide two forms of identification to enter a system or service. It combines two different factors of authentication together to prevent an attacker from getting hold of an account or resource.
The first factor is typically something the user knows, such as a password, and the second factor is something the user has, such as a token or an app on their mobile device.
For example, the system might prompt the user to enter their password and a code generated by a token or an app on their phone.
Online services, financial, healthcare, and other sensitive applications widely use 2FA, where security is paramount. The goal of 2FA is to ensure that only authorized users can use an account or a resource and to prevent fraud, hacking, or any other security breaches. By adding an extra layer of security, 2FA makes it much harder for attackers to gain unauthorized access.
Two-factor authentication (2FA) is commonly implemented through an SMS message or an authentication app, like Google Authenticator or Authy, that generates the code.
Situations where a higher level of security is needed commonly use 2FA. The financial services sector, online banking and payment systems, and other sensitive applications such as email, social media, and cloud storage often use them.
A subset of multi-factor Authentication is Two-factor Authentication (2FA), which is commonly known as two-step verification.
Clear about Two-factor authentication (2FA)? Now, let’s get started with multi-factor authentication (MFA).
What is Multi-factor Authentication (MFA)?
The mechanism of multi-factor Authentication (MFA) is just like 2FA. However, it requires multiple methods of authentication from separate categories of authentication methods. This helps to ensure that a person seeking access to a system or information is who they claim to be and makes it more difficult for unauthorized users to gain access. Examples of authentication methods that can be used in MFA include user passwords, user security tokens, and fingerprints. By requiring more than one form of authentication, MFA provides an added layer of security.
Factors Used for an MFA
An MFA can generally use three types of factors:
- Knowledge-based Factors: It can be a password or a personal identification number (PIN); only that the user has.
- Possession-based Factors: A security token or a mobile phone makes up for a possession-based factor.
- Inherence-based Factors: Inherence-based factors include fingerprint or facial recognition.
With multi-factor authentication (MFA), a user must provide at least two factors to access the system or service. For example, the system might prompt the user to enter their credentials, and then it may send a code to their mobile phone via text message or generate it using an app. The combination of the password and the code sent to the phone verifies the user’s identity, and compared to 2 FA, it is much harder for an attacker to obtain both the credentials and access to the phone.
Multi-factor authentication (MFA) is commonly used in corporate environments and situations where access to sensitive data is involved, such as government, health care, and various services like AWS. MFA can also secure resources over the internet against unauthorized parties or control on-premise or cloud-based systems.
Now that we know what Multi-factor authentication (MFA) is, let’s move on to the difference between Two-factor authentication (2FA) and multi-factor authentication (MFA).
Read Also: Phishing Vs Vishing – The Key Differences Explained
What are the Key Differences Between Two-factor authentication (2FA) and multi-factor authentication (MFA)?
When we talk about the differences between MFA and 2FA, the number of authentication factors is an obvious difference. Apart from that, it’s important to consider that MFA uses three authentication factors, each with different security levels and convenience of implementation, and the verification process may demand different amounts of time for each.
Let us discuss some of the differentiating factors.
Is Two-factor Authentication (2FA) is more secure than MFA?
Thus, in terms of security, MFA is generally considered to provide a higher level of security than 2FA. This is because MFA makes it more difficult for an attacker to intercept a system or information, as they would need to have multiple forms of authentication rather than just two.
2FA requires two separate methods of authentication, typically their credentials and a security token or a code sent to their phone or email.
MFA, on the other hand, requires more than two methods of authentication. Apart from using the same methods as 2FA, it also uses additional methods like biometrics.
Ease of Application When It Comes to 2FA and multi-factor authentication (MFA)
Two-factor authentication (2FA) is generally considered easier to implement and use than MFA because it involves only two authentication methods. These methods are relatively simple and easy to use; most people are already familiar with them.
Multi-factor authentication (MFA), on the other hand, requires more than two methods of authentication. It can use the same methods as 2FA, but sometimes it also involves additional methods like fingerprint, facial recognition, etc. These additional methods of authentication can be more complex and may require additional hardware or software to be implemented. Due to this, it becomes more difficult for users to set up and use.
Flexibility of 2FA vs. MFA Authentication
Two-factor authentication (2FA) and multi-factor authentication (MFA) differ in terms of flexibility because MFA is more flexible than 2FA.
2FA typically requires two authentication methods, so it is relatively simple, but they may not provide enough flexibility to meet the needs of all organizations. MFA requires more than two authentication methods and can use a combination of different authentication methods. This enables a wider range of security options that an organization can customize to meet its specific needs. This allows for a wider range of security options.
Scalability Between multi-factor authentication (MFA) and Two-factor authentication (2FA)
Multi-factor authentication (MFA) is generally more scalable than two-factor authentication (2FA). As 2FA typically demands two methods of authentication, they may not be able to handle a large number of users or a large number of applications. However, MFA requires more than two authentication methods and can handle a larger number of users and applications.
Cost Of These Authentications: 2FA and MFA
MFA may be more expensive than 2FA, as it may require additional hardware or software and ongoing maintenance costs. Implementing Two-factor authentication (2FA) is typically less expensive as it can use existing technologies without requiring additional hardware or software.
In MFA, the use of hardware or software, such as biometric scanners, security tokens, or smart cards, can increase the cost. Apart from that, MFA requires ongoing maintenance and support costs and the cost of updating the system when new authentication methods become available. This makes MFA a costly technology to use.
So these are the basic difference between the 2-factor authentication vs. multi-factor authentication debacle.
Two-Factor Authentication Vs. Multi-Factor Authentication
As already discussed, 2FA uses 2 factors to verify a user’s identity, while MFA uses more than 2. The latter tends to be more secure, but it depends on the chosen methods and can be less convenient for users. Depending on the implementation, 2FA can still be considered part of MFA. A more standard implementation of MFA includes 3FA, which requires three factors.
