SHA 256 vs SHA 512: Key Encryption Algorithms Differences Explained!
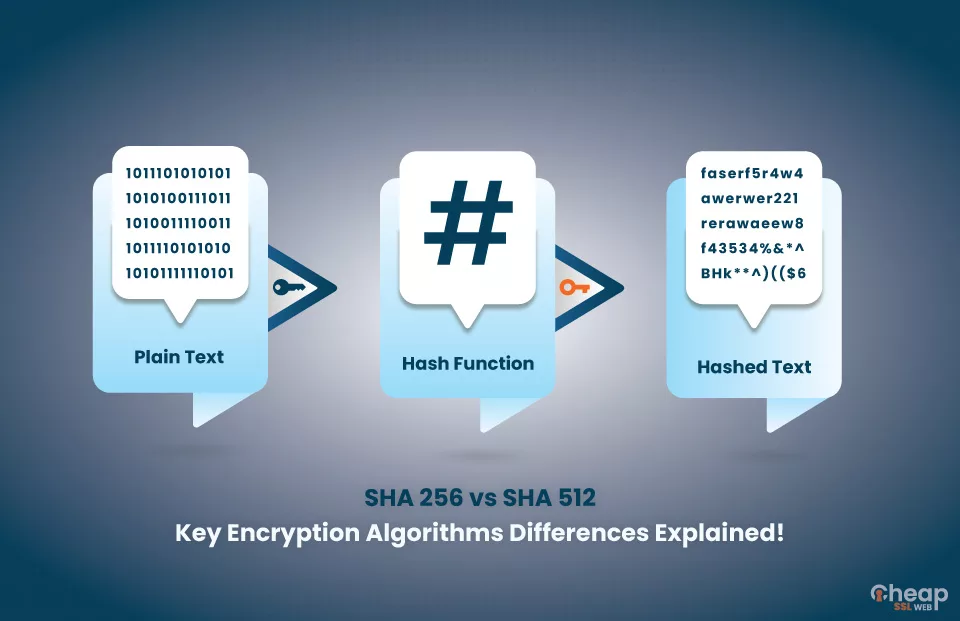
SHA 256 vs SHA 512 – Which One is More Secure?
Data is the currency of modern-day businesses. However, as this data is in large volumes, it needs to be protected before it can be used. Hashing algorithms are one of the best ways to secure the data, but SHA 256 vs SHA 512 is a tough clash when it comes to choosing one for your operations.
Both of these hashing algorithms are best in their unique way. However, when it comes to choosing one of them, the decision can be critical. Therefore, in the upcoming sections, we will analyze both of them in a comprehensive way. We will begin with basics and end where you will know which hashing algorithm is right for you. We will also help you with finding the best SSL certificates.
What is a Hashing Algorithm in SSL Encryption?
In the current online security landscape, more powerful encryption means more security. Hashing is one of the powerful encryptions that can serve for an extended period of time.
Most cyberattacks are targeted at transmitting data. Therefore, hashing ensures that the transmitting data cannot be intercepted. How?
In a hashing mechanism, your plain text message is converted into a minimal digital signature. The best thing is that no matter the length of your message, the generated digital signature is of a fixed length. On top of that, the produced signature, aka hash or digest, is irreversible, no matter what.
There are numerous complex calculations involved in the generation of the hash. Hence, if there is even a minor change, the hash keys will be entirely different, informing you about the tampering. If, in any case, the hacker gets hold of the hash key, the original message cannot be intercepted.
Hashing in SSL!
When it comes to the use of hashing in SSL, it works to authenticate if the received information is right or wrong. Here is how!
The function of the secure socket layer is to ensure data integrity while in transit. When the certificate authority issues a code signing certificate to a user or organization, the certificate is hashed and digitally signed.
On the receiving side, the digital signature will be verified, and the hash function will be used to re-hash the certificate back. If there is any tampering, the incorrect hash will prove it, and the certificate will be deemed invalid.
This is an overview of the working of hashing in SSL.
What is SHA 256?
There are two families of hash functions, SHA-1 and SHA-2. The SHA 256 belongs to the SHA-2 family of hashes. SHA-1 is a cryptographic hash function that was designed around 1995 and was disapproved for cryptographic usage after 2010.
Note: SHA-1 was disapproved after a collision attack was discovered by Google and CWI Amsterdam in 2017.
SHA 256 is a hashing algorithm that was published in 2001 when the SHA-1 was losing its strength against brute force attacks. The hashing algorithm was a joint effort between National Security Agency and NIST.
The number 256 has a unique significance in its functionality. The number signifies the length of the final hash value or digest. It means that no matter how big the plain text is, the hash algorithm will always produce a 256-bit hash value.
Here are some key characteristics of the SHA 256 algorithm!
- The length of the message, cleartext, or plaintext should be less than 264 bits. Yes, the message can be of any length, but for random hash values, it should be in the comparison area.
- The digest length or the final hashed value should be 256 bits.
- All the 256-bit hash algorithms should be irreversible. It means that the plaintext should not be retrievable if the digest is available or vice versa.
Padding bits
The padding bits are a concept in hashing where additional bits like 0 or 1 are added to complete the block. Let me explain!
The cryptographic algorithm manages the input provided by you in blocks. Hence, if the block is 512 bits and there are five more bits left to complete the entire message apart from the last 64 bits, five padding bits will be added to it. These bits will be 1,0,0,0,0.
What is SHA 512?
Just like SHA 256, SHA 512 also belongs to the family of the SHA-2 family of hashes. Though it is not as widely used as SHA 256, it is also a powerful hashing algorithm.
The characteristics of SHA 512 are almost similar to SHA 256, with the difference of the following!
- The length of the produced hash or digest is 512 bits.
- The input message is broken down into block sizes that will be in multiples of 1024 bits.
- The message should be irreversible. The plaintext should not be retrievable if the digest is available or vice versa.
Other than this, the padding bits work in the same way as in SHA 256. The block size is 1024. If there are seven bits left other than 128 bits to complete the input or the next multiple of 1024, padding bits should be added to complete the input. The padding bits would be 1,0,0,0,0,0,0.
Note: Other than padding bits, length bits are also required to complete the entire input bits. There 64 length bits in SHA 256 and 128 bits in SHA 512 hash algorithm. You can calculate these bits by applying the modulus to the original plain text without the padding bits.
What are the Various Versions of SHA?
We have highlighted only SHA-1 and SHA-2 so far. However, there are SHA-0, SHA-3, and many other sub-versions of them. Let’s discuss all of them!
| SHA Versions | Description |
| SHA-0 | Block size – 512 bits Hash digest – 128 bits Collision level – High Rounds of operations – 64 Weaknesses – Vulnerable to collisions Security level – Low Applications – It is used to verify the integrity of files. |
| SHA-1 | Block size: 512 bits Hash digest – 160 bits Collision level – Medium Rounds of operations – 80 Weaknesses – Vulnerable to collisions Security level – Low Applications – It is used for HMAC. |
| SHA-2 | Block size – 512/1024 Hash digest – 256/512 bits Collision level – Low Rounds of operations – 64/80 Weaknesses – Prone to preimage attacks Security level – High Applications – Security apps, blockchain, cryptocurrencies, and protocols. |
| SHA-3 | Block size – 1152/1088/8 Hash digest – 224/256/384/512 bits Collision level – Low Rounds of operations – 24 Weaknesses – Prone to Practical collision and Near collision attacks Security level – High Applications – Ready to replace SHA-2 whenever required. |
Note: Among the explained versions, the SHA-2 and SHA-3 are the safest SHA algorithm versions.
SHA 256 vs SHA 512 – Differences Explained!
So far, we have drilled down all the SHA versions. Now, let’s contrast SHA512 vs SHA256 in detail!
| Factor | SHA 256 | SHA 512 |
| Security | SHA-256 is a secure algorithm and is the most widely used. It is computed with 32-bit words. | SHA-512 offers better security than SHA-256, but it is not widely used as of now. It is computed with 64-bit words. |
| Compatibility | SHA 256 is compatible with Apple, Android, Blackberry, Chrome, and Windows OS. It is also supported by Chrome, Firefox, Internet Explorer, Mozilla, Opera, and Safari Browsers. | SHA 512 is supported by the Windows operating system when TLS 1.2 is not in use. |
| Applications | SHA 256 is used in authentication protocols. It comes in handy in password hashing in Unix and Linux. Cryptocurrencies can use SHA-256 to verify transactions. | SHA 512 is used in email address hashing and digital record verification. Just like SHA 256, it is also useful for password hashing and in the blockchain. |
| Hash Size | The hash size of SHA 256 is 256 bits. | The hash size of SHA 512 is 512 bits. |
Conclusion
The use of hashing algorithm in SSL is a pivotal element as it secures everything from top to down. As there are two options here, it is best to go for the SHA-256 as of now because it is widely adopted by all businesses. You can also pick SHA-512 if you want, but it may have some limitations, such as compatibility issues. Make sure you carefully study the SHA 256 vs SHA 512 comparison to make an informed decision.
As the certificate authority follows the latest security standards like SHA algorithms while providing certificates, you must pick the right one. Cheap SSL Web is one of the finest choices for you as they offer all types of genuine security certificates.
