Elliptic Curve Cryptography (ECC) Encryption Algorithm Explained
Elliptic Curve Cryptography is an excellent alternative to RSA! Read ahead to find out how!
Cyberattacks have grown significantly in the last few years. Since the pandemic year 2020, the surge in the number of cyberattacks has been huge. As per recent stats, businesses suffered over 50% cyber attacks per week in 2021. Moreover, 43% of cyberattacks are targeted at small and medium-sized businesses. So, why is this happening? One of the prime factors is the lack of powerful encryption. A powerful yet not that popular way of securing data while transacting online is Elliptic Curve Cryptography.
Unlike many other encryption techniques, ECC encryption involves a mathematical function that is easy to compute in one direction but is tough to reverse. This is the reason it is preferred, just like the RSA encryption.
If you aren’t aware of the remarkable ECC cryptography, we have this extensive guide for you! Read and discover more!
What is Elliptic Curve Cryptography?
Elliptic Curve Cryptography, aka ECC, is a key-based method of encrypting data online. We know that whenever the data is shared on the web, it is encrypted to ensure security.
ECC does this by using a pair of public and private keys for both encryption and decryption. It is often compared to the RSA (Rivest–Shamir–Adleman) algorithm, as the RSA algorithm follows the same approach but with prime numbers.
Unlike RSA, ECC uses the concept of elliptic curves to generate security between key pairs.
Why is Elliptic Curve Cryptography Algorithm better than RSA?
Ok, we know that elliptical cryptography uses the mathematical concept of elliptical curves to ensure safe data transfer over the web. So does RSA, then how is ECC encryption better?
Smaller key size
Encryption is not an easy process. Creating random security keys every time, storing them safely, and applying them to plaintext is a process that is tough. But, as it is done by a machine, we don’t have to worry, but if the keys are long, it can affect the system resources. As the storage space required is more for longer keys, ECC can help here.
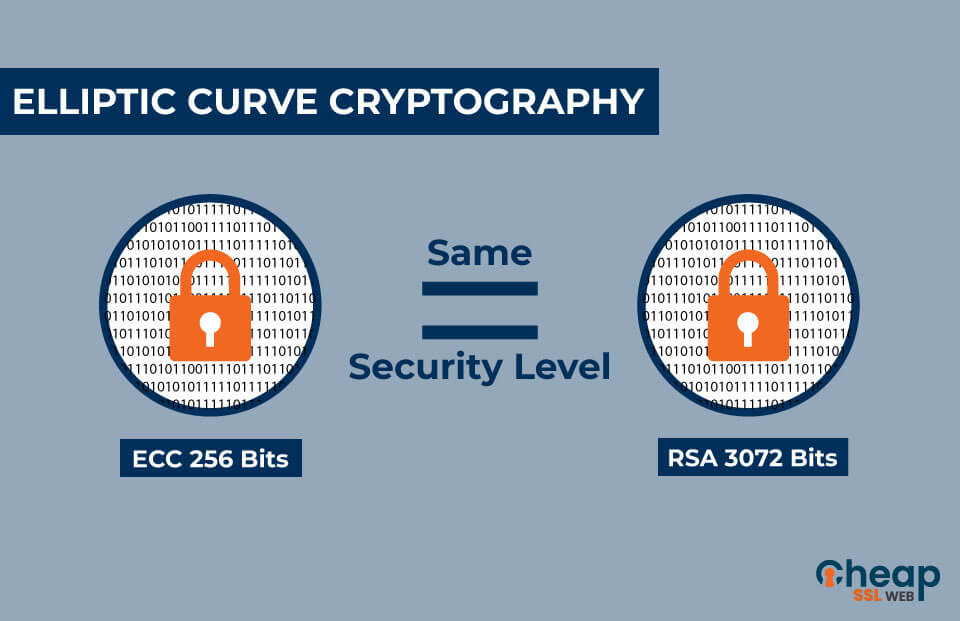
One of the key benefits of Elliptic Curves Cryptography over RSA is the key size. Unlike RSA, the key size of ECC encryption is significantly smaller. Here is an example!
For the same level of security, the key length of an RSA key and ECC keys are mentioned below!
| ECC Key (in bits) | RSA Key (in bits) |
| 160 | 1024 |
| 224 | 2048 |
| 256 | 3072 |
| 384 | 7680 |
| 521 | 15360 |
Faster Key Creation
One of the ideal features of the Elliptic curve cryptography algorithm is that it generates keys super fast. For example, the generation of a private key in ECC is just like generating a random integer which is faster and more efficient. On top of speed, any key in the range of the function is a valid private key.
Lower computing power
The ECC algorithm in cryptography is useful for encryption while generating smaller keys. But, this is not it. The ECC encryption algorithm also uses lower computing power and battery than the RSA. Hence, saving resources for other processes.
It can be scaled
Again, let’s bring in the concept of the keys here. We know that the keys produced by ECC are smaller in length and faster to generate. The smaller length of the keys makes ECC easily scalable. On the other hand, when RSA keys reach the length of 3072-bits or over, ECC performs over 100% faster.
Ideal for low-powered devices
The ECC encryption uses smaller keys that are directly related to the efficient use of resources. As the computing power required is less, ECC is ideal to be used on mobile and IoT devices.
Is Elliptic Curve Algorithm in Cryptography Secure?
Well, the basic thing that distinguishes ECC from other encryption methods is the key size. So, even if you are using a bigger key size to encrypt the data, it will be smaller as compared to other methods. Moreover, the security will be more than other methods. On top of this, the internal efficiencies that this method has are what makes it secure.
A few drawbacks of ECC Encryption
No matter how powerful or secure an encryption technique is, there is always room for improvement. ECC encryption is a technique that excels in various ways but still has some drawbacks, such as
Vulnerabilities
There are two types of vulnerabilities that ECC has, and both of them are targeted at private keys. These vulnerabilities are side-channel attacks and twist-security attacks.
- Side-channel attacks: The side-channel attacks aim to leverage the benefit of leaked information from a tamper-resistant device. This critical information is extracted by keeping a check on the power and timing of the tamper-resistant device. Attackers can target machines with various types of side-channel attacks like fault analysis attacks, differential power attacks, simple power attacks, and simple timing attacks.
In these attacks, attackers aim to mess with the power and timing of devices like hardware security modules in the hopes of getting access to secret security keys.
- Twist-security attack or fault attack: These attacks are aimed at getting the victim’s secret key somehow. Though the process of these attacks is long, it is super effective if all the conditions are met. In a twist-security attack, the malicious actor injects a carefully selected public key that does not lie on the ECC curve that can be easily reversed.
The twist-security attacks can be subdivided into various subcategories like invalid curve attacks, small-sub groups attacks, and invalid-curve attacks against Montgomery ladders. If the attacker is knowledgeable enough, the twist-security attacks are easy to implement. But, anyway, there are a lot of conditions to meet.
Tough to implement
The above-described vulnerabilities are way less harmful than this one. Though the implementation of ECC is theoretically possible, it practically challenges the experts. This is the reason RSA has been widely used as compared to ECC.
RSA, unlike ECC, is faster and simpler in both encryption and verification. ECC has a steeper learning curve and hence is tough to implement. Incorrect implementation of ECC can lead to private key leaks that can lead to unauthorized access.
What are the Various Algorithms of ECC?
Based on the mathematics of elliptic curves over finite fields, ECC can provide various algorithms!
ECC Digital Signature Algorithm
The Elliptic Curve Digital Signature Algorithm (ECDSA) is used by cryptocurrencies like Bitcoin and Ethereum. The security features of ECC enable cryptocurrencies to sign the transactions securely. ECDSA is used for classical curves, and the Edwards-curve Digital Signature Algorithm (EdDSA) is used for twisted Edward curves.
ECC Key Agreement Algorithms
The ECC key agreement algorithms allow for secure key exchanges over an insecure channel. They are of various types like ECDH, FHMQV, and X25519.
ECC Encryption Algorithms
ECC encryption algorithms like ECIES and EECC allow for semantic security.
What are the Advantages of the Elliptic Curve Cryptography Algorithm?
Well, if we take an overall look, there are countless benefits to the Elliptic curve cryptography algorithm. Here are some of the prime ones!
Super secure
One of the chief advantages of ECC is security. ECC works on an algorithm that works easily in one direction but is tough in the reverse direction. As ECC deals with the prime factorization of prime numbers, it is super tough to reverse, which ensures security.
Fast
As the key size in ECC is smaller than RSA, the processing time and computing power required to process them is less. Hence, it is ideal for mobile and IoT devices.
Fewer resources
Unlike RSA, ECC, when used, requires less memory on the servers. This ensures faster response time and throughput.
Is ECC the best for you?
Elliptic curve cryptography is used in various organizations today, such as Facebook, Cloudflare, etc. So, is it ideal for you?
As per the current scenario, RSA is the most widely used cryptosystem. It is used by over 90% of SSL certificates, while ECC is used by 4%. Now, by statistics, it may seem like it is not for you. But, trust us, the adoption of ECC is on the rise.
If you have a website that requires powerful security and is complex, ECC could be the perfect match for you. However, note that the use of ECC requires implementation, and it needs to be handled carefully.
Is ECC supported by all browsers?
Well, one of the drawbacks and factors that ECC is not well-adopted to is the ability to support all the browsers.
As of now, ECC is available on Chrome, Opera, and Apple OS for all platforms.
Wrapping Up!
As per the current web security scenario, ECC is one of the best alternatives to RSA in SSL encryption. Therefore, it is best to plan ahead and be future-ready to adopt it. ECC may not be dominant today, but it will surely be in the future, not to forget the rising use of mobiles for which it is an indispensable choice.
