What is a Certificate Revocation List [CRL]?
Understanding the Basics of Certificate Revocation List (CRL) for Secure Online Communication
Have you ever thought about what happens when someone revokes a certificate before its expiration date, who manages it, and where it goes? The answer to all these queries is – the Certificate Revocation List.
Suppose someone no longer trusts an SSL certificate. In that case, the CA positions it in a CRL file, which functions as a mechanism that addresses the revocation of digital certificates securely and efficiently. This article will explore what a CRL is, its importance, alternatives, and much more.
What is a Certificate Revocation List (CRL)?
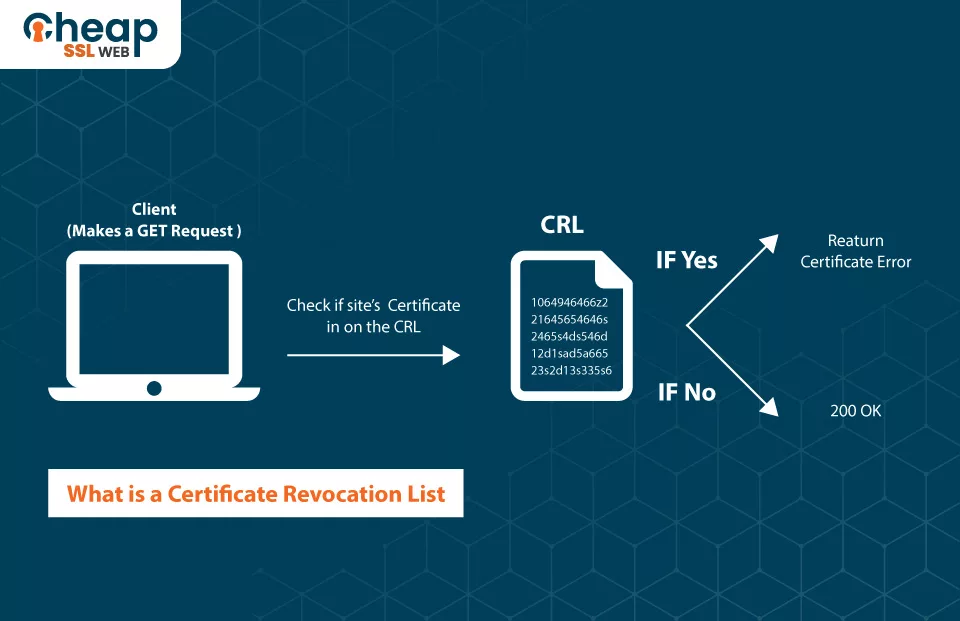
A Certificate Revocation List is a record containing digital certificate information that a certificate authority has invalidated prior to its planned end date.
In accordance with Internet Engineering Task Force’s (IETF) RFC 5280, the CRL is a signed data structure and time-stamped file that the issuer of the CRL or a CA periodically issues to denote the cancellation status of digital certificates. As per National Institute of Standards and Technology (NIST), it is an inventory of withdrawn public key certificates produced and digitally marked by a CA.
The certificate authorities generate CRLs at regular intervals (every hour, every day, or every week) and distribute them to relying parties. By checking the record, relying parties, such as a web browser, can confirm the validity of digital certificates before engaging in online communication.
Note: This list does not contain any information related to lapsed certificates.
What are the contents of a CRL?
Although different CAs may include varying content in their CRL files, typically every CA lists some standard information such as:
- The title of the issuer
- The extension of the certification
- The CN of the certificate
- The CA will disseminate the following CRL file on a specific date.
- The signature algorithm used for the certificate
- The serial numeral of the certificate
- The basis behind the withdrawal
What are the causes behind canceling a certificate?
There are “n” number of causes behind canceling a certificate; let’s explore some of those:
- The certificate proprietor has entirely discontinued the operations.
- Someone has stolen or compromised the secret key associated with the certificate.
- Someone has modified the user details in the certificate.
- The certificate holder has disregarded the terms and conditions of the CA’s certificate policy.
- The certificate owner no longer holds the domain for which the certificate was issued.
- Someone replaced the original certificate with a new one from a different issuer.
What is the significance of a CRL?
The Certificate Revocation file plays a vital part in preserving the safety and reliability of digital certificates within a Public Key Infrastructure (PKI). By checking the CRL list, entities, such as web browsers and other applications, are able to confirm the present situation of digital certificates and ensure that the allocating CA has not vetoed them. This helps prevent the use of compromised certificates for malevolent objectives, such as mimicking a legitimate website or intercepting encrypted transmissions.
Besides all of this, the lack of a CRL can even uncover users to diverse cyber threats or security concerns, such as:
- Monkey-in-the-middle attack
- Malware infections
- Identity theft
- Economic loss
- Hacking, etc.
Is there any difference between Certificate Revocation List and Certificate Transparency Log?
Before explaining the answer to this question, it would be much better first to understand what Certificate Transparency Log, also known as a CT log, is. CT is a public log of digital certificates that have been issued to a particular domain by CAs. This log contains various information, such as public key details and the issuer’s identity.
Even though both of these files (CRL and CT) work with X.509 certificate, they have a completely different purpose and objective. The main objective of the CT log is to allow website proprietors to observe all certificates publicly issued for their respective domains to fend against potential malevolent entities. The CLR’s main objective is to defend PKI’s security and integrity by checking the revocation status of digital certificates and stopping website users from visiting such websites.
Apart from that, there are two observable distinctions:
- CT log file does not enclose any details regarding the revoked certificates.
- You can’t edit, delete, add, or insert any entry (certificate) in a CT log file, but that’s not the case with the other one, as CRL entries can be edited.
What is the alternative method to CRL for managing the cancellation of digital certificates?
There are two alternative methods to CRL for managing the cancellation of digital certificates, and those methods are:
- OCSP (Online Certificate Status Protocol)
- Delta CRL
OCSP (Online Certificate Status Protocol)
Earlier, when you were visiting a website, your browser used to check if the digital certificate was valid or if it had been revoked and the URL had been added to the CRL. This whole process involved downloading a large list of revoked certificates that took a lot of time.
Instead of downloading that large list, your browser asks the CA or OCSP responder whether the certificate is valid or revoked. The CA uses the “serial number” of the certificate to cross-check the details present in the CRL. After checking the certificate’s validity and revocation status, the browser sends a small message (OCSP response) indicating whether the certificate is “good” (valid), “revoked” (no longer valid), or “unknown” (cannot be currently verified).
Another OCSP method that is much more instantaneous and straightforward is OCSP stapling. With this method, there is no necessity for a browser to ask the CA for the OCSP response directly. The website itself incorporates its OCSP response to the certificate sent to the browser, thus making the process more efficient and improving the browsing experience.
Delta CRL
A Delta CRL is a supplementary certificate list that only includes the changes made since the last update of the main list. So, instead of downloading the entire list, probing for the details in a concise and updated list is better. It’s especially valuable for institutions that often withdraw certificates, as the primary certificate list becomes lengthy, and exploring an individual URL becomes challenging.
Drawbacks of CRL status check
Here are some of the drawbacks of CRL status check:
- Time-consuming: Status checks can be time-consuming, especially when the list is enormous and possesses numerous entries.
- Delay in authentication: If the list is not updated frequently, authentication may be delayed while waiting for the latest list to download.
- Frequent updates: CRLs need to be revised repeatedly to stop reneged certificates from being accepted, and any intervals in updating could permit the approval of reneged certificates leading to security concerns.
- Browser compatibility: Each browser addresses CRLs in an irregular way (not in the same manner), which gives birth to safety issues. Till the time it’s not an EV cert, few of the browsers will only inspect the validity of the domain’s certificate without paying any attention or authenticating the complete chain of certifications needed for verification.
Conclusion
A Certificate Revocation List plays a vital role in defending the security and integrity of digital certificates within a PKI. The list contains rescinded certificate details, and relying entities use it to affirm the validity of certificates before engaging in online communication. While CRLs are a classic method of handling the cancellation of digital certificates, alternative strategies such as OCSP and Delta CRL also exist.
