Why Password Salt and Hash Make for Better Security?
How Secure is Password Hash with Salt?
Passwords are a primary defense against unauthorized access to personal accounts and sensitive data. However, relying solely on plain text passwords can leave systems vulnerable to attacks. This is where password salt and hash come into play, offering a robust solution to enhance password security.
In this article, we will understand what password salting and hashing are and explore why and how password salt and hash improve security.
What is Password Salt?
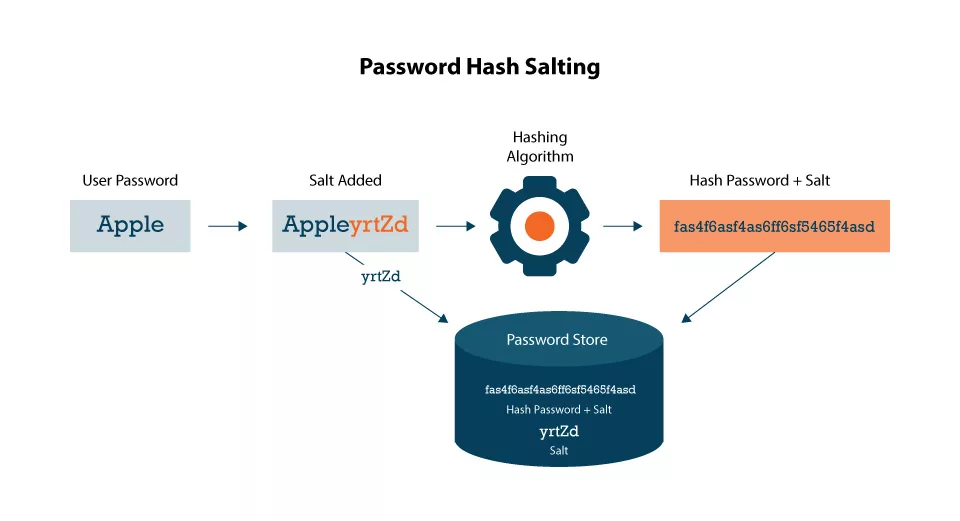
To fortify password security, it is essential to introduce randomness into the password. This is where password salting comes into play. A password salt is a randomly generated value (a string of thirty-two or more characters) added to a password before it is hashed. The salt value is typically securely stored alongside the hashed password.
Salting your password is like adding a unique ingredient to your recipe. Introducing a randomized value to each password before applying the hashing process makes the resulting hashes distinct, even if the passwords are the same. This signifies that an attacker would need to generate a fresh set of rainbow tables for each unique salt, thereby significantly amplifying the computational resources required to crack passwords.
What is Password Hash?
A password hash results from applying a cryptographic hashing algorithm like SHA-256, Argon2, etc., to a plaintext password and converting it into a fixed-length, irreversible string of hexadecimal characters.
The resulting string is unique and bears no resemblance to the original password. For instance, the password “Secure2023” might be transformed into a hash value like “45b90cf4e8719e9d.” The beauty of hashing lies in its one-way nature, making it almost impossible to reverse-engineer the original password from the hash.
How Salting Makes Password Hashes More Secure?
Salting plays a crucial role in enhancing the security of password hashes. Here’s an explanation of how salting makes password hashes more secure:
- Unique Salt for Each Password
- Complexity Against Attacks
- Slow Downs Password Cracking
Unique Salt for Each Password
Salting involves adding a randomly generated value to each password before hashing. The salt is unique for every password, even if multiple users have the same password. This means that even if two users have the password “password123,” their salted hashes will be different. In this way, salts add a level of individuality and prevent attackers from leveraging precomputed tables like rainbow tables, as they would need to generate separate tables for each unique salt, which will be a troublesome task.
Complexity Against Attacks
Salting increases the complexity of password-cracking attempts. Without salt, attackers could quickly identify patterns or common passwords by comparing hashed values. However, with the introduction of salts, the resulting hashes are entirely different, even for identical passwords. This complexity thwarts standard attack methods like brute-force or dictionary attacks, where attackers systematically try different password combinations.
Slows Down Password Cracking
The presence of salts significantly slows down the process of cracking passwords. Generating hashes for each possible password attempt becomes much more time-consuming and resource-intensive due to the need to calculate unique hashes for every salted password. This acts as a deterrent to attackers, as the increased computational requirements make it impractical to crack passwords at a fast pace.
Salting makes password hashes more secure by introducing uniqueness, complexity, and computational overhead. It mitigates the risk of password attacks and significantly strengthens the overall security of stored passwords.
How Password Salt and Hash Work Together?
The system generates a random salt value when users create or update their passwords. This salt is then integrated with the user’s password, and the resultant combination is hashed using a secure hashing algorithm.
The salt and the hashed password are stored in the system’s database. When the user tries to log in, the system retrieves the salt and hash associated with the account, applies the same hashing algorithm on the provided password and stored salt, & compares the resulting hash with the stored value. If they match, access is granted.
The Combination of Password Salt & Hash Against Cyber Attacks
The combination of password salting and hashing serves as a formidable defense against various types of attacks, like:
- Brute-force Attacks
- Dictionary Attacks
- Rainbow Table Attacks
- Credential Stuffing Attacks
- Database Lookup Attacks
Brute-force Attacks
Attackers employ a trial-and-error approach, systematically trying different password and username combinations until they find the correct one. The introduction of salt and hash significantly increases the time and computational resources required for cracking passwords, making brute-force attacks highly impractical.
Dictionary Attacks
In these attacks, criminals utilize a dictionary containing commonly used words to crack passwords. However, by incorporating password salt and hash, the resulting hashes are unique and unrelated to the original passwords or any dictionary entries. This makes it highly challenging for attackers to match hashed values to pre-existing dictionaries.
Rainbow Table Attacks
These attacks rely on large, pre-computed tables of passwords and corresponding hashes. Each password’s hash becomes distinct by introducing salts, rendering rainbow tables ineffective. Attackers would need to generate separate tables for each unique salt value, making the attack impractical.
Credential Stuffing Attacks
In these attacks, leaked or breached passwords from one system are used to gain unauthorized access to other accounts where the same password may have been reused. Password hash and salt protect against this threat by ensuring that even if an attacker obtains hashed passwords, they cannot easily determine the original passwords, preventing the success of credential stuffing attacks.
Database Lookup Attacks
Criminals attempt to extract valuable information by sending SQL query statements to the website’s database. The combination of password salt and hash safeguards against these attacks, as the hashed passwords stored in the database are useless without knowledge of the salts, making it problematic for malicious actors to recover the unedited passwords.
By incorporating the password salt and hash combination, systems can mitigate the risk of unauthorized access and protect user accounts. It defends against brute-force and dictionary attacks, thwarts rainbow table and credential stuffing attacks, and ensures the security of stored passwords even in the event of a database lookup attack.
Conclusion
In conclusion, password salting and hashing play vital roles in strengthening the security of personal accounts and sensitive data. Adding random salts to passwords before hashing makes the resulting hashes distinct, preventing attackers’ attempts to crack passwords using precomputed tables or common patterns easily. Salting imbues the passwords with uniqueness and complexity, significantly amplifying the computational resources required for password cracking, rendering such endeavors highly impractical.
Additionally, password hashing changes plaintext passwords into irreversible strings of characters while ensuring that the plaintext password cannot be reverse-engineered from the hash. This introduces an additional layer of security, making it burdensome for attackers to gain unauthorized access.
The combined utilization of password salt and hash forms a robust defense against various cyber-attacks, including brute-force attacks, dictionary attacks, rainbow table attacks, credential stuffing attacks, and database lookup attacks. By implementing these techniques, systems can effectively mitigate the risk of unauthorized access, safeguard user accounts, and uphold the security of stored passwords.