Encoding Vs. Encryption: Explaining the Difference
Encoding Vs. Encryption: Let’s compare and understand the difference between two major web security algorithms.
In the world of cybersecurity, encoding and encryption are two important techniques that play a key role in protecting data from third-party access. In addition, both these technologies are used for incorporating an additional layer of security. For example, data can be encoded before being encrypted, which can make it more difficult for an attacker to decrypt the data if they are able to gain access to it. Due to this reason, encryption Vs. encoding is often talked about in cybersecurity, and often both terms are often used interchangeably.
However, they are different techniques with different purposes, so it is important to understand the difference between encoding and encryption. So, before we decode encryption vs. encoding, let us understand both of them individually.
What is Encoding?
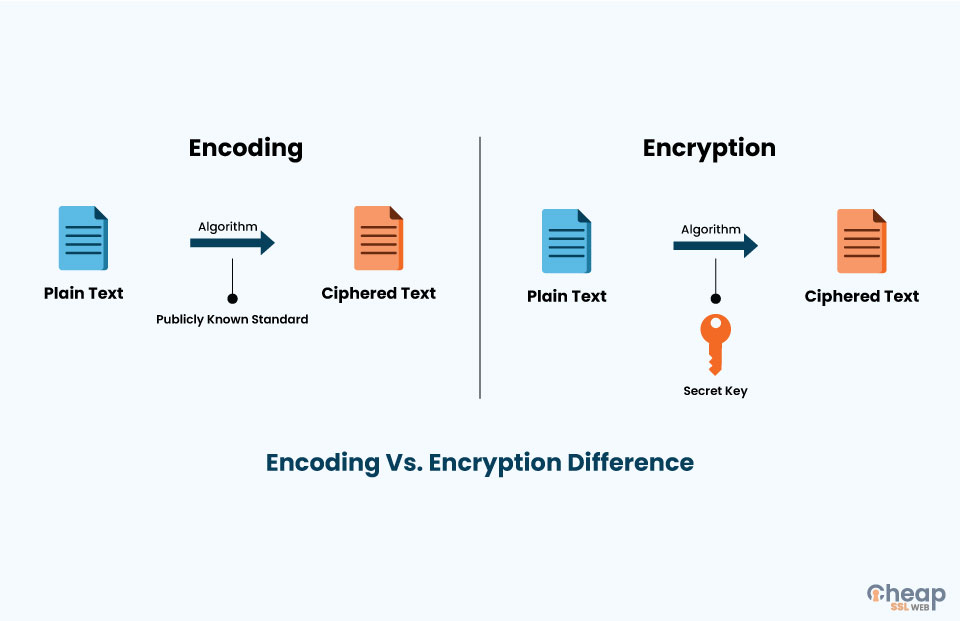
Encoding is the use of a particular technique for changing data into a totally new format. It is a reversible process that usually involves the application of popular techniques to encode and then again decode it in its original format.
Encoding has found its use in places where data cannot be transferred in its original form between applications and systems, thus keeping the data’s usability and integrity intact. However, it is not used for securing data as it is quite easy to reverse it back to its original state, so it does not take much for any attacker to decode the data in case they already have some encoded data. So obviously, encoding is not used for security purposes.
These are some examples of encoding:
- Base64 Encoding: This is a commonly used technique for encoding binary data into ASCII text format and is often used for encoding data such as images, audio, and video files over a network or for storage in a database.
- URL Encoding: This is another type of encoding that encodes special characters in a website’s URL so that they are safely transmitted in the web space.
- Hexadecimal Encoding: This encoding technique represents binary data in a hexadecimal (base 16) format. Therefore, it is commonly used for representing binary data in a more human-readable form and is often used for debugging and troubleshooting purposes.
- ROT13 Encoding: This is a simple form of encryption that involves rotating the letters of the alphabet by 13 places. It is not considered secure, but it is often used to obscure spoilers or other sensitive information.
- ASCII Armor: This is a technique used to encode data in a format that is resistant to corruption or tampering commonly used for encoding digital signatures and other cryptographic data.
These are some examples of the types of encoding that are used in cybersecurity. Encoding is an important technique for protecting data, but it is not the same as encryption and does not provide the same level of security.
Now, let us take a closer look at encryption, something that one cannot think of the Internet without. This will help us understand encryption vs. encoding.
What is Encryption?
What makes the Internet a safe and secure place for the end-users is ‘encryption.’ It is a process of converting a piece of data or information that is unreadable and literally impossible to decode for any cybercriminal or hacker. But why is this process secure?
Encryption uses ‘cryptographic keys’ to encrypt the data at the client’s end. For decrypting the data, the receiver’s system may or may not use the same key. Depending on the type of keys used for the encryption and decryption of data, the process is divided into two categories:
– Symmetric Key Encryption
– Asymmetric Key Encryption
Symmetric Key Encryption: As the name suggests, this type of encryption is symmetric. So when the sender sends a piece of data to the receiver, they use something called a ‘private key’ for encrypting the data. Here, the information of the private key stays confidential between the sender and the receiver.
As the receiver receives the encrypted information, they use the same private key for decrypting it. Symmetric key encryption is often used in banking for encrypting personally identifiable information (PII) is required for transactions and data storage purposes.
Asymmetric Key Encryption: Asymmetric Key encryption does the opposite of the symmetric encryption method. So, in this process, the encryption key is public and available to all, but the decryption key is private and known only to the intended recipient. This enables secure communication as there is no prior distribution of a shared secret key between the sender and the recipient.
The private and public keys are mathematically related, but it is computationally infeasible to determine one key based on the other. Asymmetric key encryption has found its use case in digital signatures, Blockchain and Public key infrastructure (PKI).
So this was all about encryption and encoding.
What is the Difference Between Encoding and Encryption?
The primary differences between encryption and encoding are as follows:
● Purpose
Encryption is used to secure data converting the data into an unreadable format to protect it from unauthorized access. Encoding is used to represent data in a different format to protect the integrity of data for storage or transmission.
● Security
Encryption offers a higher level of security than encoding. The reason is quite simple. The former uses complex algorithms and a specific key to convert data into an unreadable format that is literally impossible to crack by machines or humans. On the other hand, encoding converts data into a distinct format that is more human-readable, but when compared to its counterpart, it is quite possible for a machine or human to decode.
● Confidentiality
Encryption protects sensitive information and keeps it confidential, making sure that only and only authorized parties can access the data. However, encoding does not offer the same level of confidentiality.
● Algorithm
Encryption employs specific kinds of complex algorithms such as AES (Advanced Encryption Standard), RSA (Rivest-Shamir-Adleman), or DES (Data Encryption Standard) to encrypt the data. Encoding, however, uses different techniques that are typically simple and do not require a key to encode or decode data, such as Base64, Hexadecimal, etc., to represent the data in a unique form.
● Reversibility
Encoding is reversible, meaning that the original data can be recovered with the algorithm that is publicly available. Encryption, on the other hand, is a reversible process, so naturally, the original data can be recovered with the use of the correct decryption key, but it is not publicly available like the former.
● Key
Encryption uses a pair of public and private keys to encrypt and decrypt data. The private key is used to encrypt data, and the public key is used to decrypt it. Without a public key, no one can access the data as it is in an unreadable format. Encoding does not use any key, so the encoded data can be retrieved or decoded by anyone who has a proper grasp of tools or technologies, as they won’t need any key to decipher data.
● Compliance
Different regulations like HIPAA (Health Insurance Portability and Accountability Act) and PCI-DSS (Payment Card Industry Data Security Standard) often require security regulations, thus ensuring the security of confidential information. However, encoding does not have to meet any security requirements.
● Tamper Proofing
Encryption provides tamper-proofing of data, so in case any unauthorized party tries to modify the data, it will be detected as the decryption of the tampered data will fail. But encoding does not provide this level of tamper-proofing.
So these are some of the differences between encoding and encryption. Here is a table for better understanding.
Encoding Vs Encryption Algorithm Comparison
| Parameters | Encoding | Encryption |
| What is it? | It is the process of transforming data into such a format that it can be by a different type of system using publicly available algorithms. | It is the process of encoding data securely so that only the authorized user who knows the key or password can retrieve the original data for everyone else; it is just a random string of characters. |
| Purpose | Protection of the integrity of data | Transforming data to keep it secret from others. |
| Used for | Maintaining data usability. | Maintaining data confidentiality. |
| Reverse Process | With the help of decoding, the original data can be retrieved. | With the help of decryption, the original data can be retrieved. |
| Key requirement | The encryption key is not required to decrypt the data and get the original data. | The encryption key is required to decrypt the data and get the original data. |
| Security Level | The security of the encoded is less as it can easily be decoded. | The encrypted data is more secure. |
| Compliance | It does not comply with any security regulatory bodies. | It complies with HIPAA and PCI-DSS for security regulations. |
| Tamper-Proofing | Encoding does not provide an encryption level of tamper-proofing. | Encryption provides tamper-proofing of data. |
| Example of Algorithm | ASCII, UNICODE, URL encoding, Base64. | AES, RSA, and Blowfish. |
| Application | Viewing special characters on the web page | Securely sending a password over the internet. |
Apart from these two terms, another term that confuses people is hashing, which is why there is a lot of confusion regarding encoding vs. encryption vs. hashing. Hashing maps data of arbitrary size to data of a fixed size. It is a one-way function that takes an input and returns a fixed-size string of characters which is called the ‘hash value,’ ‘message digest,’ or ‘digital fingerprint.’ The same input will always produce the same hash value. But even a small change to the input will produce a very different hash value.
So which of these technologies is needed for your website? Let’s find out.
Encryption Vs. Encoding: Which One is Important for Your site?
As we compare encrypt vs. encode, the obvious winner here is encryption. Be it security or confidentiality, encryption wins. However, the application of complex algorithms makes it a superior technology to use on your website.
The application of algorithms in encoding is to represent data in a different format that is more efficient, compact, or standardized, while the application of algorithms in encryption is to encrypt the data to ensure that only authorized parties can access it.
Concluding Lines
It’s important to understand the differences between encoding, hashing, and encryption. It is because using the wrong technique for a given situation can have serious consequences. Encryption and encoding are different processes serving different purposes in security.
For example, using encoding to secure sensitive data would not provide any security, as the original data can be easily reconstructed from the encoded representation. On the other hand, using encryption to compress and decompress data would be inefficient and unnecessary. Therefore, it is important to use the appropriate technique for a given situation to ensure that the data is protected and properly transmitted or stored.
