What is a Root Certificate and How to Download It?
Internet security is extremely essential today to stay protected from undesired viruses. Having robust security measures can ensure the privacy of your data and help you prevent any fraudulent activities. SSL certificates are an essential and first line of control when it comes to web security.
They are like CCTV cameras for your house that keeps a watch on everything that you do within your browser. However, the root certificate is the fundamental aspect that makes SSL certificates workable.
So in this blog, we will understand everything about root certificates, their working, and their role in web security. Let us start!
What is a Root Certificate?
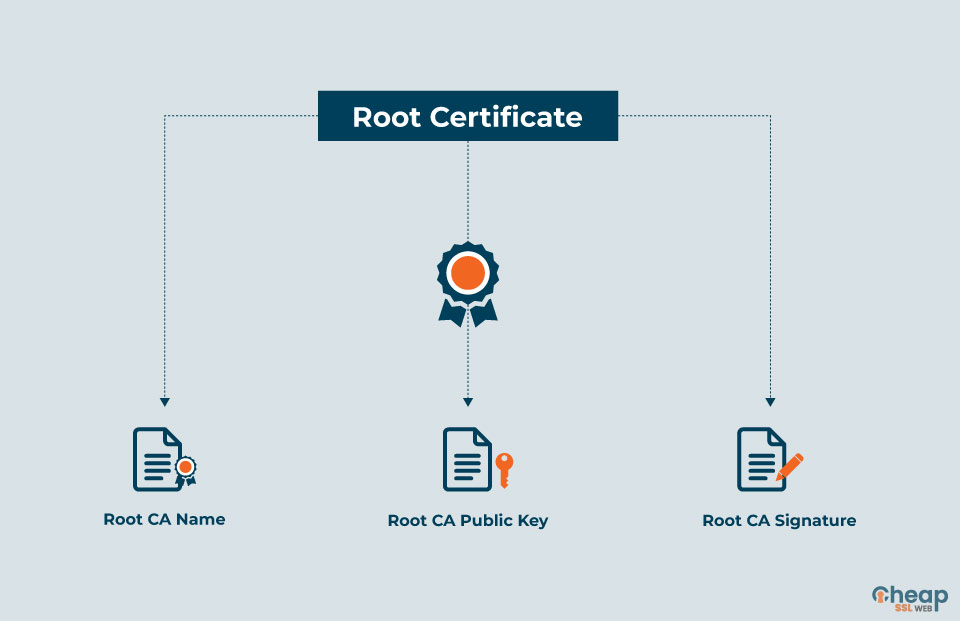
A root certificate, in simple terminology, can be understood as a certificate issued by a trusted certificate authority which is used to verify the authenticity of the owner of a website.
A trusted certificate authority, on the other hand, is an entity which is entitled to authenticate and verify the owners of websites. All participants, operating systems, and browsers must agree on a set of trusted CAs to make this model functional.
In the SSL ecosystem, any person can generate a signing key and leverage it to sign a new certificate. But, that certificate isn’t considered valid until directly or indirectly signed by a trusted CA.
Therefore, the SSL ecosystem is created out of a trusted relationship. Whenever a device validates a certificate, it gets compared to a list of trusted CAs. Only when the match is found the certificate (such as PositiveSSL or PositiveSSL Wildcard) is considered valid. Above all, the root certificate is seen as the most important as it can only be issued by a trusted Certificate Authority.
Root Store
A place where all the root certificates are stored is known as the Root Store. A root certificate is the first to be checked by the protocol in the certification process. Every internet browser has its own root stores consisting of public keys they trust.
When a user connects to a server, a public key is sent by the server that the user can verify. The protocol verifies the certificate’s authenticity and the CA’s signature. Hence, a root certificate ensures complete security for your web browser and facilitates a safe internet usage experience.
What are Certificate Chains?
A list of certificates that usually starts with an end-entity certificate and is followed by more than one self signed root certificate is known as the certificate chains. Here are some of its key properties:
- Every certificate issuer must match the subject of the following certificate in the list.
- Every certificate must be signed by the secret key by the next certificate in the chain.
- The last certificate in the list is considered a trust anchor delivered by a trustworthy procedure.
The certificate chain is often also known as the certification path, which implies the chain of trust refers to your SSL certificate. For an SSL certificate to be trusted, the chain, server, intermediate, and root must be traced back to the trusted root where it was signed off.
Intermediate Certificate
It branches off root certificates similar to the branches of trees. They work as a middleware in between the server certificates and the protected root certificates before issuing any certificate to the public. There needs to be at least one intermediate certificate in a chain to obtain a root certificate. However, there can be more than one intermediate certificate in a chain.
Server Certificate
It is the certificate issued to a particular domain that the user needs coverage for.
To sum it up, certificate chains are leveraged to check if the public key and other supported data contained in an end-entity certificate belong to the subject or not.
How Do Root Certificates Work?
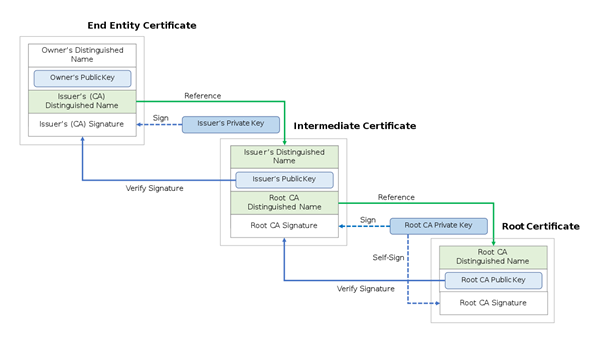
As explained earlier, root certificates are formed to verify the identification of a user who is creating data for the transmission to the end user in an encrypted format. A certification authority issues the trusted root certificate. The certification functions like a chain of command, with the root certificate, considered the chain’s root.
To execute the process, the signature on the end-target certificate is authenticated using the public key of the following certificate, whose signature is verified by the next certificate. It goes on in the same way until the last certificate in the chain is reached, which is a trust anchor, and hence the end-entity certificate can be trusted.
What are Intermediate Certificates?
Due to the surged need for good and reliable Public Key Infrastructure (PKI), root CA is now being replicated to increase its numbers. However, having multiple Root CAs can be an issue as it could lead to management and fraudulent issues.
To fix this problem, the introduction of intermediate certificates was done. The Root Certificate authorities assigned their tasks to Intermediate CAs to streamline the process.
An intermediate certificate is a substitute to a root certificate as a root certificate has various security layers to ensure its keys remain unobtainable. So the intermediate certificate works as a Chain of Trust between a root certificate and an end entity certificate.
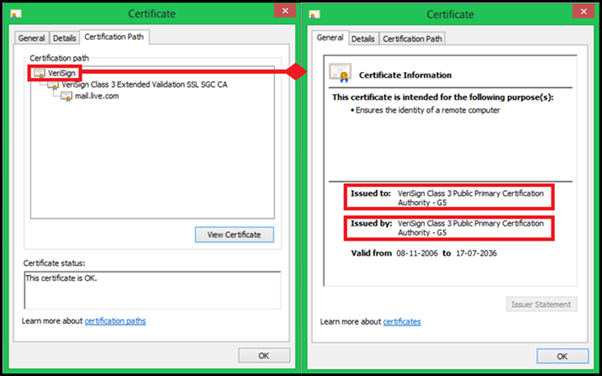
A root certificate can be differentiated from an intermediate certificate by viewing the certificate itself. If the ‘Issued by’ and the ‘Issued to’ fields are the same, then it is a root certificate; else, it is an intermediate. Another way to distinguish between the two is by looking at their Certification Path. The path to root certification will always appear at the top.
Here is an example to follow:
How to Download the Root Certificate?
A trusted root certificate only needs to be installed if you are notified by your computer system that the certificate of authority is not trusted on the machine. It usually occurs when using a private certificate server instead of an established public certificate of authority.
Process to Download the Root Certificate
- Open your web browser in the system that requires a certificate.
- Next, navigate to your local certification server in the browser (In some systems, it would be there by the name of client certificates).
- Select the option, Download a CA certificate, CRL link, or certificate chain, as needed.
- Pick the desired certificate of authority from the given list and select the Base 64 Encoding method.
- Select the Download CA certificate link.
- Choose the ‘Open’ option when asked to open or save the certificate.
- After the certificate window gets opened, select Install Certificate.
- On pressing the Install Certificate option, a Certificate Import Wizard will appear.
- Choose the ‘Next’ option in the wizard.
- You will get prompted for the Certificate Store.
- Select ‘Place all certificates in the following store’.
- Further, choose the Trusted Root Certification Authorities store.
- Click the next button and complete any remaining steps of the wizard.
Once you have gone through the above-given procedure, the next step is to add the certificate snap-ins leveraging the Microsoft Management Console (MMC).
How to Add Certificate Snap-Ins?
- Launch MMC (mmc.exe).
- Select File > Add/Remove Snap-ins.
- Next, choose Certificates and then choose Add.
- Select My user account.
- Again choose the Add again option and this time select Computer Account.
- Relocate the new certificate using the following commands: Certificates-Current User > Trusted Root Certification Authorities into Certificates (Local Computer) > Trusted Root Certification Authorities.
This is how you can download the self signed root certificate and enjoy a secure internet browsing experience.
How to Import a Root CA Certificate?
Now that you know how to download the root certificate, next is the process to import the root ca certificate.
There are two methods to import root CA certificates on a Windows system:
- Certificate Import Wizard
- MMC Console
Certificate Import Wizard
1) First, open your browser and navigate to SSL certificates in the settings.
2) Open the download certificates, and right-click on the selected downloaded certificate.
3) Choose the option ‘Install Certificate’.
4) The certificate import wizard will open. Click Next.
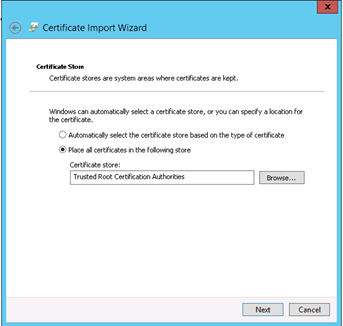
5) Select the option ‘Certificate Import Store’.
6) Scroll down to the second option to browse the Trusted Root Certificate Authorities store.
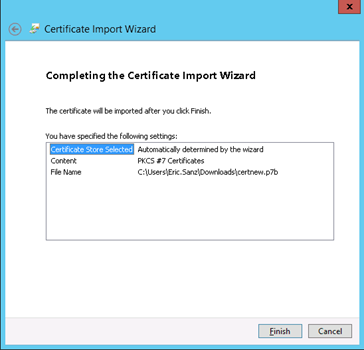
7) Complete the imported root CA certificate process
MMC Console Method
1) Press Win + R to open the Run utility.
2) Type MMC in the box.
3) Press Ok.
4) Add Certificate Snap-in by going to File > Add/Remove Snap-in.
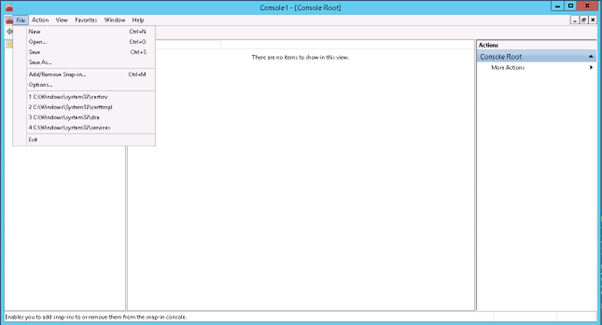
5) Select Certificates and Press the Add Button
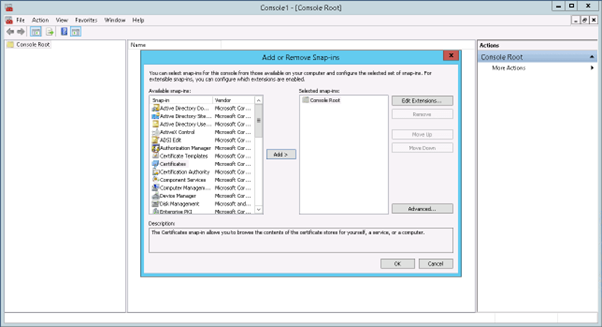
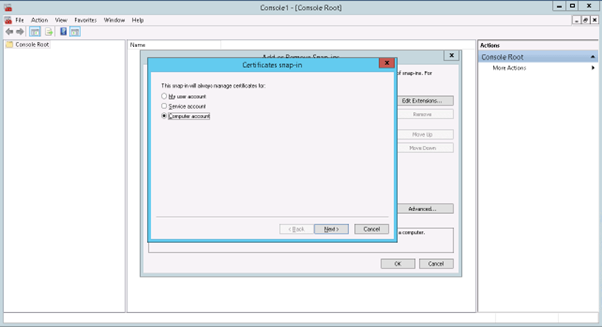
6) Choose the User or Computer in which you want to create the Certificate Snap-In and Click Next.
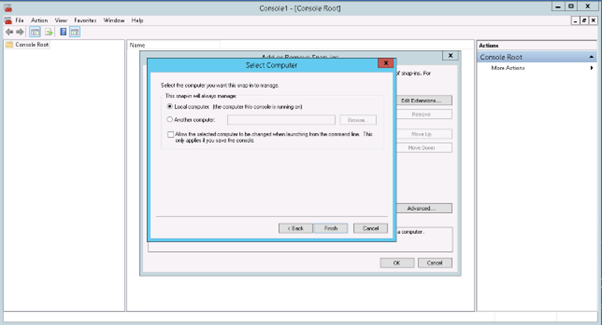
7) Select the local computer if you wish to install the certificate on the same computer.
8) Select Certificate and click Ok
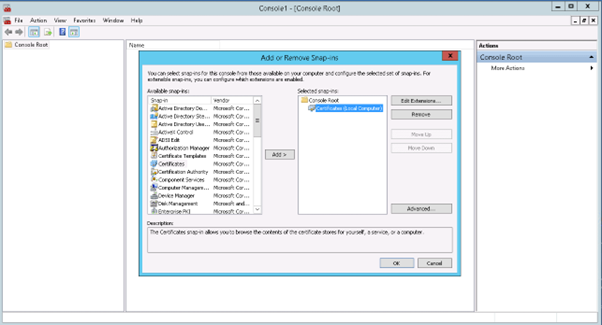
9) Load MMC
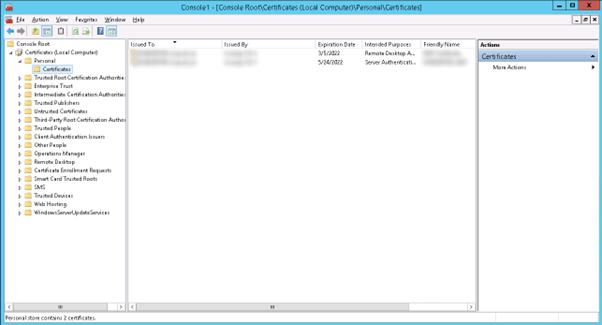
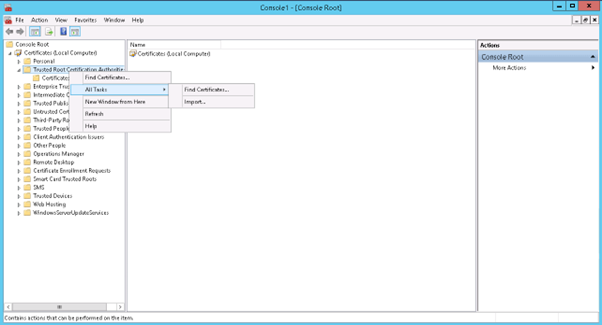
10) Import the certificate by right-clicking on the Trusted Root Certificate Authority.
11) Next, Select All Task -> Import.
12) Certificate import wizard from MMC would prompt. Click on Next.
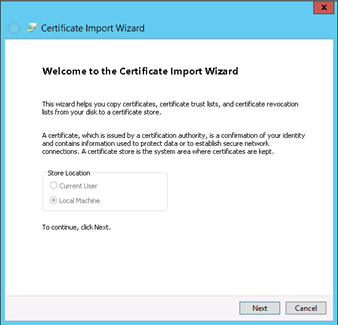
13) Browse the root CA certificate
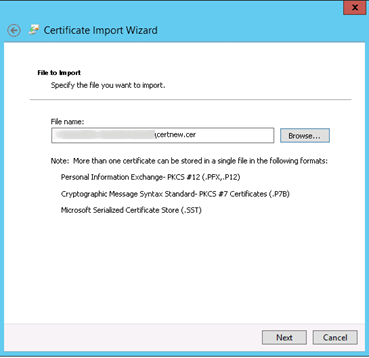
14) Select the certificate store and choose the second option to browse the Trusted Root Certificate Authorities store.
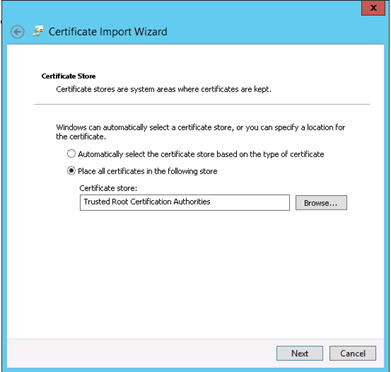
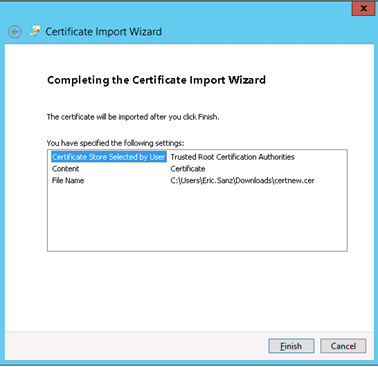
15) Completing the import root CA certificate process
Conclusion
Data security is of prime importance, and you must be acquainted with every technology related to it. So now that you know about the root certificate and its functioning, you can further learn more concepts of cybersecurity and upgrade your skills in the field.
