What Is a Root CA Certificate, and Where Can I Use It?
Learn About Root CA Certificate and Complete Your SSL Certificate Chain
Among the various digital issues today, online security and privacy are the prime ones. When you search for something online, you are subconsciously giving away a lot of information to the web. Now, lucky for you that Google marks the website as secure or insecure based on its SSL certificate, or all of our crucial data would easily fall into the wrong hands. An SSL certificate acts as the sole parameter that defines the security of the website. However, its foundation is something else, and it is the Root CA certificate.
If a website is not secure, you might have encountered the error, “this site may be insecure.” It is a common error that Google shows you when a website is insecure. This thing questions the SSL certificate, which goes back to the intermediate certificate and that points back to the CA root certificate.
Online security is crucial, but what is the root CA certificate, and where can you get it? We will briefly discuss everything in the article. Just keep reading!
What is a Root Certificate?
The root certificate is the major or, should we say, the primary node of the entire public key infrastructure. It serves as the fortress from where all the legitimate commands of the infrastructure originate.
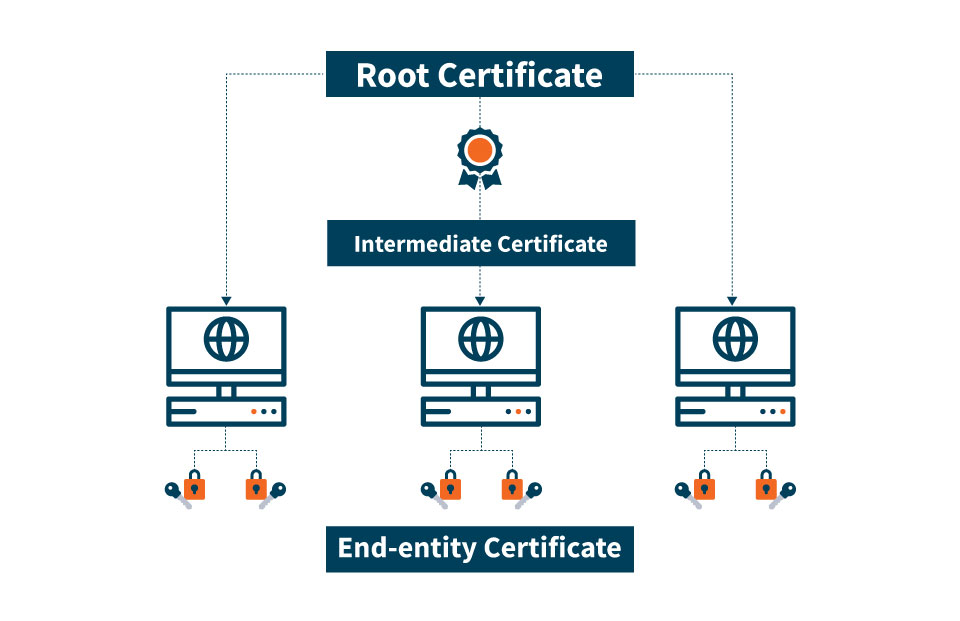
To understand the root certificate, we have to understand the certificate chain first. Whenever a user searches for something and clicks on a website link, the SSL certificate of that website is checked by the browser.
Now, by default, every machine has a root store that contains all the necessary root certificates. When the browser checks the obtained SSL certificate with the root store, the root store returns a signed version of the SSL certificate, if indeed it is a legitimate one.
The CA root signs the SSL certificate and returns it. When the browser sees that the certificate is signed with the private key, it opens the website in front of the user.
Basically, what’s happening behind the scenes is that the browser is following the certificate chain to check if the SSL certificate is legit. The structure of the chain is as follows!
CA Root Certificate Vs Intermediate Certificate Difference Explained
CA Root Certificate
The root certificates are the pivotal elements of the public key infrastructure. They are self-signed by their CAs. As a CA is a certified authority, all the SSL certificates are under a specific CA. As the root certificate is one of the pivotal elements of the PKI, it needs to be protected at all costs.
Intermediate Certificates
The second key entity in the PKI is the intermediate certificate. The cool thing about the intermediate certificate is that it directly falls between the root certificate and the leaf certificate (SSL certificate), and there is a reason for this.
You see, the root certificates are too crucial to get compromised. As they are the perfect embodiment of trust, they need to be protected at all costs. Hence, to insulate them, the certificate authorities issue an intermediate root.
So, whenever an SSL certificate is required to be signed, the intermediate root signs the certificate, and it becomes legit. The intermediate root is signed with the private key, which makes it trustworthy.
Now, it is not mandatory that there is only one intermediate root between the root certificate and the SSL certificate. There can be more than one intermediate certificate too in the chain.
What Constitutes a Trusted CA Root Certificate Authority?
On the web, trust is classified as Social and Technical Trust.
Technical trust is always dependent on Social trust. However, to be a trusted or legitimate Root certificate authority, there are various things that need to be fulfilled. For example, audits, public scrutiny, and other strict requirements.
It is pretty obvious that if you are a new Certificate Authority (CA), you will start issuing certificates way before getting verified. The verification process is simple and straightforward! When your SSL certificates are used for enough time without any issue, you will get verified.
Once this happens, you will get the roots added to the root stores of various operating systems like iOS and Android. Thus, you become a trusted root certificate provider.
By definition, a trusted root certificate is a special type of X.509 digital certificate. It can be used to issue other certificates.
What Is the Lifespan of Root Certificates?
If you are getting the message, “this site may be insecure,” it can be due to the fact that the lifespan of the certificate has depleted. Usually, this happens only in the case of SSL certificates that are mis-issued or have security issues.
In the case of the root certificate, it is highly unlikely as the age of these certificates is more than the SSL certificate. An SSL certificate has a lifespan of 2 years, whereas the lifespan of a root certificate is 25 years or more.
How Does the Browser Know if the SSL Certificate Is Legit?
Well, if the root certificate has signed the SSL certificate, it is enough to prove that the SSL certificate is legit. But, the browsers check some of the basic points to assure its legitimacy. Here are some of those points!
- The browser checks the validity date.
- It is checked if the certificate has ever been revoked.
- Digital signatures by the root CA are verified.
How to Get a Root Certificate From CA?
Well, there is no need for you to download the root certificate on your machine. Why? They are already pre-installed on it; secondly, they come stored in the root store of the operating system.
So, whenever you get an untrusted SSL certificate, the system will warn you. Moreover, the root stores are also auto-updated with the new CA certificate file. So, no need for a manual update.
However, if you want to undertake the root certificate download for any reason, you can do it from the support page of the service provider.
Final Words on CA Root Certificate
So, this is all about the root certificate! It is the key element of the public key infrastructure that ensures the security of the user data. However, as the root certificate is a crucial element, it needs to be protected in all cases. Thus, an intermediate certificate is connected to it.
It is done to ensure safety as the intermediate certificate can sign the SSL certificate on its behalf. The root certificate has a longer lifespan as compared to the SSL certificate, which is pretty obvious as it is a governing entity.
