What Is Intermediate Certificate And How To Download It?

A Complete Guide to Intermediate Certificate, Its Working, and Where to Download It
As companies implement public key infrastructure, they have to choose from several security components. From getting the SSL certificates to executing hash functions, and encryption, among others, it is essential to build secure communication channels.
The key aspect of this secure communication is protecting the integrity of data and information stored or shared through the web. An intermediate certificate is a part of the public key infrastructure. It is required to establish a connection between the client and the sender. There are other ways of ensuring the same functionality. They come in the form of root certificates and server certificate. We will go through the details of the intermediate certificate authority and its related components to obtain a better understanding.
What is an Intermediate Certificate?
Intermediate certificates emerge from and to benefit from root certificates. Protecting and preserving the private keys of root certificates, which are issued and handled by certificate authorities (CAs), is essential. Hence, an intermediate certificate is one of the layers of security added here for the benefit of a root certificate.
An intermediate certificate is a substitute, or a proxy certificate used to protect themselves from the whims of supplying a root certificate. Issuing a server or leaf certificate to ensure SSL implementation puts the CAs at risk.
So, they use intermediate certificates to protect themselves. They will use the private key generated with the intermediate certificate to issue SSL certificates. So, while the end result stays the same, the CAs are protected from any sort of risk of giving away their root folder.
What are Root Certificates Then?
A root certificate is the main document or authentication managed by CA’s. Every device has pre-listed certificate authorities, and when browsing the web or doing any activity, the platform will be checked against the issued certificates.
For instance, when you open a website, there is a small lock sign left of the URL. This lock sign means that the said website has obtained an SSL certificate. If you are able to access the website without getting a warning message, it means the CA is registered into your device’s root access folder.
All the root certificates residing on the device has public keys. Any certificate signed with a private key will utilize the device’s root access folder or connect with a third-party app before letting the user interact with the platform.
Root certificates authorities are at the dead center of this entire working model. Without a root service and certificate, we cannot facilitate a secure connection between the sender and receiver.
Understanding the Root Program
We know that for an intermediate or SSL intermediate certificate to be authentic, it must be connected to the root certificate and its organization, called a CA. The CA further relies on the root folder and the pre-downloaded certificates. The entire system, or the Root Program, as we are calling it, works under some strict guidelines.
The CA/B Forum provides the fundamental requirements for the root program. In addition to this, organizations like Microsoft, Google, Apple, and Mozilla, which provide access to the majority of the digital infrastructure across the globe, have set their own guidelines.
For all these organizations to set strict guidelines, they need Trust. Because without trust, any SSL, root, and intermediate certificates are useless. It is essential to have social and technical trust.
- Social Trust: Social trust is the verification of the CA by the public. Every CA has to undergo public scrutiny, complete audits, and follow the rules. Besides satisfying all the requirements, social trust also includes the market perception of the brand and its image.
- Technical Trust: Technical trust comprises the Root CA’s ability to ensure the security of the certificate. Technical trust also comes from the technical robustness of the certificate. It means how strong the implementation part is. Remember that a technically strong CA will get better trust from the public.
Every certificate authority has to show its mettle before they are accepted in the industry as a trusted provider. And this trust does not come easy. Plus, it is not possible for a CA to start signing off root certificates from the first of its operation. Every established CA must have been working as an intermediate certificate provider before being promoted and accepted as a root certificate. At this point, their organization and root certificates are added to the devices because they have gained the requisite trust.
Certificate Chain or Chain of Trust
There is a chain of events involved when we bring in the component of an intermediate certificate. Let’s say that the website NAIAA.com wants to receive an SSL certificate to establish the required security.
For this, they will go to NSAA.CA, which is a Certificate Authority and is registered as a Root Certificate provider on the devices and third-party applications. Now, NSAA.CA does not want to reveal their public keys like this and wants to be protected.
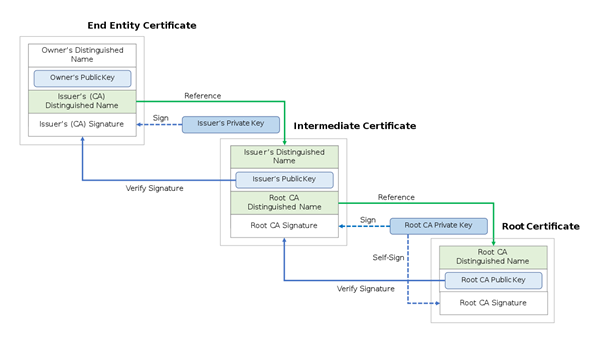
For this, an intermediary developed or hired by NSAA.CA, let’s call it ICA, will come forward to provide the certificate. In essence, the intermediate certificate provided by ICA will be digitally signed by the NSAA.CA, but it will be distributed under the name of ICA.
The final SSL certificate issued by NIA will complete this chain of events. So, we have an organization providing Root Certificate, an intermediary providing Intermediate Root Certificate, which then signs the SSL certificate.
These levels of certificate issuing authority ensure proper use of public and private keys.
So, this chain will have the following components;
- SSL or TLS certificate
- Certificate Authority
- Intermediate certificates
The chain begins with the SSL certificate. At every level, we can see the entity that has signed the certificate moving forward to the next level until we reach the root certificate authority.
Sometimes, the browsers and devices let you access the web and ask you to install an intermediate certificate. This intermediate certificate is required to complete the chain of trust and establish a connection to the source.
Difference Between Root Certificate and Intermediate Certificate
After all the readings above, the difference between an intermediate certificate and a root certificate might be clear. But let’s go through them separately here.
The Root certificate provider is a trusted and authentic CA who owns one or more than one root. These roots are embedded into the devices we use and are available via third-party providers, mostly used by browsers.
Some major providers that have these third-party root stores include Google, Microsoft, Apple, and a few others.
On the other hand, an intermediate certificate authority issues an intermediate root certificate. These intermediate roots don’t have direct access to the root access folder in the devices, nor are they directly integrated into the root stores.
However, they are linked to the trusted root certificate provider, which is integrated into the root access folder and root store. So, a chain connects both these root certificate providers, and their successful cooperation leads to adding the SSL certificate to an application or website.
So, if you are providing Root certificates, you won’t directly hand them out like a pamphlet on the junction. You will create an intermediary certificate authority and provide the SSL certificates from there.
This does two things;
- It compartmentalizes the issuance of certificates. If one of the intermediate certificate authorities is hacked, then only the certificates issued from the affected authority will be at risk. This will control the damage.
- It will make the root certificate authority completely off-limits from any kind of attacks.
So, the difference between these two types of certificates stems from their importance and implementation. Where the intermediate certificate is meant to protect the root certificate, it also helps with mitigating the risks and allowing quick damage control.
Downloading Intermediate Certificate
Root certificates are pre-installed into the system, and SSL certificates are loaded on call. However, when it comes to intermediate certificates, we need to download them separately.
As SSL intermediate certificates simplify the administration process while enhancing the security aspect, they have become an essential part of creating a secure and privacy-led web environment.
The intermediate certificate is downloaded and installed on the server. This will complete the authentication process and enable the visitors to validate the trust chain, which goes back to the root certificate.
Follow the process to download the intermediate certificate;
- Login to the server and click on SSL certificates. You will probably find it in the left navigation menu.
- Locate the certificate you want to download.
- You will find a download link. Click on it and finish the process.
With this, we have completed the core part of understanding an intermediate certificate. Let’s move on to knowing about additional aspects related to root, intermediate, and SSL certificates.
Why are Digital Signatures Important Here?
Digital signatures mean authenticating a document, only in this instance, we are talking about notarizing root, intermediate and SSL certificates. A root certificate will digitally sign the intermediate certificate. With this signature, the root certificate authority also transfers a part of the trust to the intermediate certificate.
The digital signature gets instant approval because of the root certificate’s private key. The moment an individual is presented with the SSL certificate, the public key is attached to it. With this key, the server will identify the digital signature and also find its source or who made the certificate.
This way, the browser will authenticate every digital signature included in the chain until it reaches the root certificate. So, no matter how many levels of intermediate CA certificates are added to the chain, digital signatures can help determine the root certificate and find its presence in the browser’s trust store.

Comodo Positive SSL Wildcard
Starts at $38.99
Buy or renew Comodo Positive SSL Wildcard Certificate at affordable price. Secure primary domain and all subdomains on multiple servers on a single Wildcard SSL Certificate.
Conclusion
Comodo SSL certificates are an essential part of the public key infrastructure. Their utility has only grown over the years. With intermediate certificates coming into the picture, the SSL/TLS certification has become more authentic and secure.
Making the security net wider, intermediate certificates are highly beneficial for the entire chain of trust system. For some, implementing the intermediate system can be a complex thing to discover, but it can be highly beneficial, especially for browsers that are enabled with automatic updates.
Hence, it is customary to understand the role of intermediate certificates before implementing them.
