What is AES-256 Encryption? Everything You Need To Know

What is AES-256 Encryption?
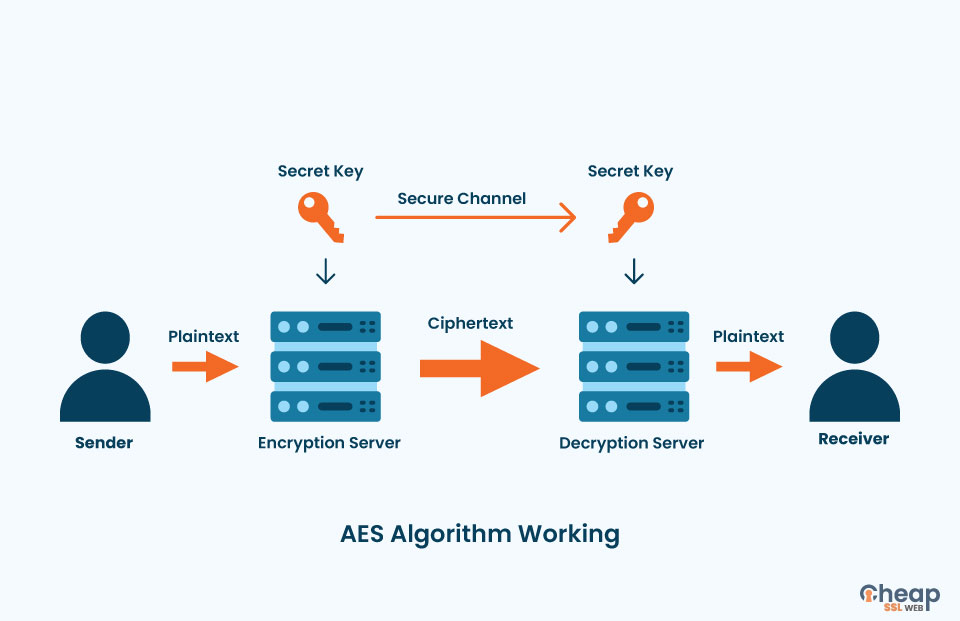
AES-256 encryption is a symmetric key cryptographic standard that is used for securing information like passwords, messages, and files by encrypting them with AES 256-bit encryption keys.
To put it in other words, AES-256 encryption applies symmetric encryption, where an identical key is used in both encryption and decryption. It makes its operation based on a unit of data, approximately 128 bits in length.
Recommended: What is AES 128 Bit Encryption? How Secure AES 128 Bit is?
“The AES-256” means 256 is the length of the encryption key in bits. The AES sets different rounds of substitution, permutation, and mixing operations. These functions are applied repeatedly (or iteratively) as a way of scrambling the letters in plaintext into jumbled-up ciphertext.
Thirdly, the specific function expansion generates a set of round keys of the original encryption key and these keys are applied to each round of encryption.
The algorithm AES-256 is considered strong due to its large key size that makes it immune to brute-force attacks. One of such measures is the strong cryptography that is applied at a number of levels; namely, the safekeeping of data, communication protocols, and cryptographic signatures.
How Does AES 256 Encryption work?
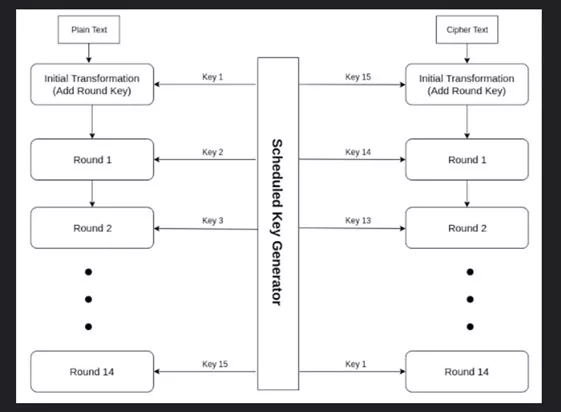
AES encryption works by using a symmetric block cipher algorithm with a block size of 128 bits.
The encryption process involves several key steps:
Key Expansion:
AES function encoded secret key size of 128,192, or 256 bits. The expansion formula generates round keys which, according to the number of rounds used for encryption, number the same. Each round key is derived from the previous one using a combination of bitwise operations, including substitution and rotation.
Initial Round:
At the first round plaintext XOR (bit wise exclusive OR) with K1 which is the first round key. This step ensures that the plaintext is combined with the key before any further transformations are applied.
Rounds:
AES consists of several rounds which number is the key size makes:
10 rounds for a 128-bit key
12 rounds for a 192-bit key, and
14 rounds for a 256-bit key
Each round consists of four main transformation stages:
- SubBytes – this stage substitutes each byte of the state to a corresponding byte from a fixed table called S-box. This non-linear substitution adds confusion to the encryption process.
- ShiftRows: Row cyclic left shift is done in this phase by moving the left column of the state matrix to the right. The top row stays the same, the second is shifted by one to a left, the third by two positions and fourth by three. This diffusion ensures that patterns in the plaintext do not remain evident in the ciphertext.
- MixColumns: Each of the states here has to go through this specific process called the MixColumns transformation that is done by some unique mathematical operations. This transformation is a one of a kind process which works on four bytes of each column using the method of modulo over a fixed polynomial. It provides additional diffusion and confusion to the data.
- AddRoundKey: In this phase, the square key for the specific round is AXORd with the matrix of data. In every round, the mixing of a byte of the state and the corresponding round key byte would occur.This step adds the key’s contribution to the encryption process.
Final Round:
During the fourth stage of encryption, all the procedures from the previous rounds are executed without the transformation of the MixColumns to simplify the decryption.
Decryption:
By applying decryption keys to the ciphertext in the reverse order, these keys transform it into the inverse. The decryption process consists of the following steps:
The inverse MixColumns and the first round of the decryption use the following sequence of steps:
- Inverse RotateRounds
- Inverse SubBytes
- Inverse MixColumns
After that the final step of the second round of the decryption happens.
AES is secure against a number of cryptanalytic attacks with as little computer time and power as possible. It is literally already referred to as the most widespread standard ever in symmetric encryption, which is used in all areas from protecting communication to data storage and ensuring the digital signatures.
Features and Importance
Key Features & Importance of AES 256 Encryption:
Features of AES-256 Encryption
- AES-256 utilizes a 256-bit key, which is in fact the strongest of all encryption levels. It would require billions of years to brute force Cryptanalysis of AES-256 today even if we were using the most advanced computing technology.
- AES-256 as a symmetric key algorithm implies that the same key is used both for encryption and decryption. So it is symmetrical encryption which is faster and more efficient than asymmetric cryptography.
- AES-256 splits data into 128-bit blocks and conducts 14 rounds of encryption in each block for generating the ciphertext. The more rounds lead to a more robust encryption method.
Importance of AES-256 Encryption
- The AES-256 is the encryption standard sanctioned by the U.S. government for protecting classified information. It is usually adopted by databases, VPNs, password managers, and many other programs which have the highest need for security at all costs.
- Incorporation of AES-256 encryption is essential for businesses to avoid data leaks and save their sensitive data. It not only makes sure you keep your customers’ trust but also helps you to prevent any kind of compliance issues and limits the harm from possible security incidents.
- AES-256 is the most mature encryption technology providing the greatest security shield against sophisticated cyber threats to data, making it the golden standard of encryption.

Is AES 256 Encryption Crackable?
Based on the search results, AES-256 encryption is considered highly secure and virtually uncrackable using brute-force methods with current computing technology:
- AES-256 has a key that consists of 256 bits. Hence, from the computational point of view, such a key would take billions of years to crack in case of brute-force attacks. Such a huge step forward in the level of protection is incompatible with the 56-bit DES which could be hacked in an instant.
- However, some attacks on theoretical vulnerabilities have been given, such as related-key attacks and known-key distinguishing attacks, that have only been shown to work on the half-cycle versions of AES, which is not the entire 14 round AES-256 implementation.
- The primary danger is these side-channel leak based attacks during which sensitive information is spilled out, but through careful implementation, these attacks can be thwarted.
- On the whole, the conclusion from the search results is that AES-256 is claimed to be the ultimate standard for encryption and yet, the technological capability is far below what it takes to crack the codes.
In conclusion, 256-bit AES is the most secure available encryption standard. Thus, any brute-force or other known attacks not presumed in this practical timeframe are impossible to break it.
What are the Applications of AES?
The applications of AES (Advanced Encryption Standard) encryption are diverse and crucial in ensuring data security across various sectors:
Wireless Security:
AES is basically established to strengthen wireless networks such as Wi-Fi and above all data confidentiality and security.
Database Encryption:
AES encrypts the data that is stored in tables of the database and prevents unauthorized access and misuse of sensitive information like PII and card details in the event of such breaches.
Secure Communications:
Email, instant messaging, and voice/video calls are just some examples of communications that are heavily used on the internet. The importance of data confidentiality is one of the reasons for their increased use.
Data Storage:
AES encrypted sensitive data on computer hard drives, USB drives, and other storage media before tossing them into the trash and therefore prevents data breaches when they are misplaced or stolen.
Virtual Private Networks (VPNs):
Its extensive use covers the provision of security to any communication between user devices and a remote server and hiding user’s data.
Secure Storage of Passwords:
AES encryption encrypts storing passwords to increase a protection level against intrusions. Thus, users’ authorization details are protected from unauthorized access.
File and Disk Encryption:
Functioning as an encryption tool for securing information when it is stored and also during transport on the devices like computers and their external storage such as USBs, and on the cloud services.
Processor Security:
Commonly found in CPUs on either side of the system to improve the speed and security in the form of the increased throughput and data protection.
Consumer Applications:
Capitalized with gadgets and apps through which the consumers use, for example SSDs, Google Cloud storage, online browsing, and Snapchat and Facebook apps amongst others.
SSL/TLS:
IPsec stands out due to the fact that it is an essential element of the data encryption protocol SSL/TLS that is used to secure communication over the internet. Similarly, IPsec is used to protect data confidentiality and integrity during transmission.
Recommended: Encrypt your Website with Trusted SSL Certificates – Starts at just $3.99/yr
Difference between AES & DES
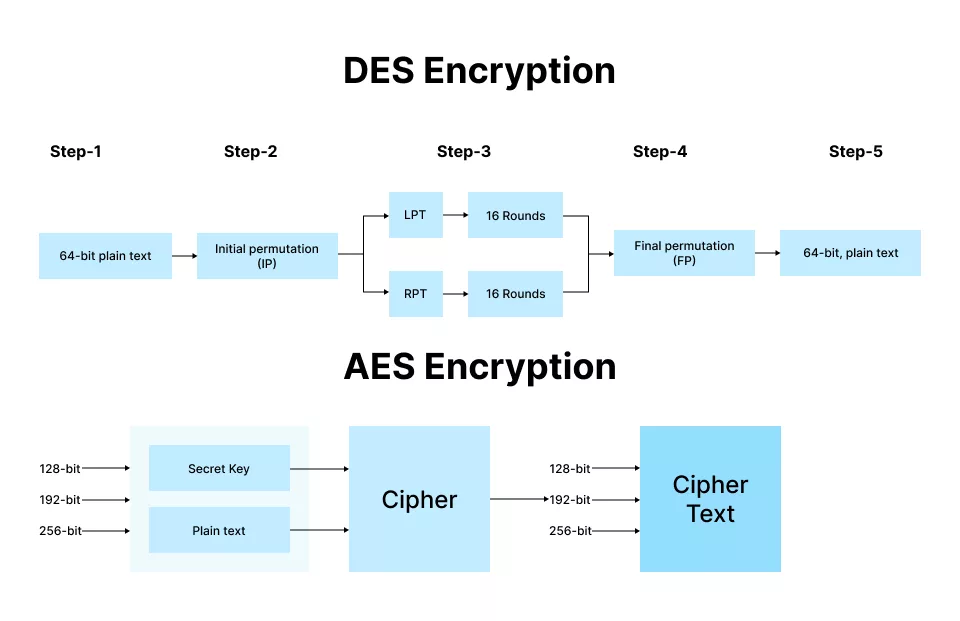
Based on the search results provided, here are the key differences in the use cases of AES (Advanced Encryption Standard) and DES (Data Encryption Standard):
| Aspects | AES(Advanced Encryption Standard) | DES (Data Encryption Standard) |
|---|---|---|
| Security Level | Through the work of the researchers, AES is seen as quite robust, with no proven successful tactics. | DES is relatively weak of the central method but is vulnerable to brute-force attacks on the hacker side, while the Triple-DES algorithm provides more secure results. |
| Government/Military Use | AES is the minimum security standard going for the United States of America in order to protect classified information. | DES was formerly government owned cryptography which ceased to be after AES replaced it due to its poor security service. |
| Performance | AES is much faster than DES and Triple DES. | DES is slower than AES. |
| Application Areas | AES is performing a primary role within databases, VPNs, password managers, wireless security systems, and other applications, breathing a very high level of security demand. | DES continues to be used primarily for backward compatibility issues; therefore, a new system should not choose DES for data confidentiality relying. |
| Key length | AES allows the use of 128, 192, and 256 bits keys. | DES uses a fixed key length of 56 bits. |
| Orientation | AES works by splitting data into blocks of bytes. | DES works with data that is grouped together into blocks of bits. |
| Design Rationale | In AES, the algorithms are publicly discussed, and the code is available for all to see. At the same time. | In DES, the rationale is closed, and only a few individuals can access the code. |
With an intensity level of 256, the AES encryption is considered a bulletproof security implementation in many areas which may include preventing unauthorized access and preserving secrecy.
Conclusion
Empower your website’s security, and construct a welcoming environment whose visitors can trust by CheapSSLWEB‘S SSL/TLS encryption solutions.
With our cost-effective SSL certificates, we provide the most advanced cyber safety measures that can protect your site’s data against any intrusive threat, guaranteeing the privacy and security of data processed between your website and its users.

