What Is SHA-256 Algorithm & How It Works?

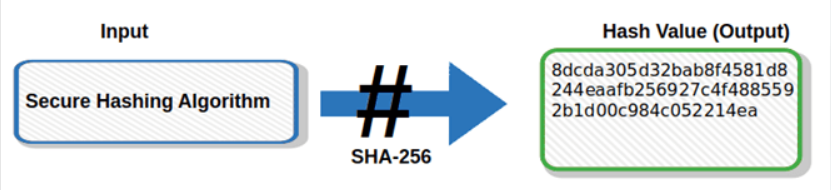
What Is SHA-256 encryption?
SHA-256 encryption stands for the hashing condition via SHA-256 algo. This algorithm includes an input message of any length of and generates a fixed length output of 256 bits that is represented in the hexadecimal form usually.
The process entails several stages, starting with padding the input message, initializing constants and applying the round after round hash function using typical arithmetic, logical operations.
The very last output of SHA-256 is a hash value of the input message, which serves as a digital fingerprint.
What makes SHA-256 special in cryptography is its resistance against attacks. Because of its structure and the complexity of the algorithms, SHA-256 makes collision and preimage attacks almost impossible.
In a collision attack, two input messages become the same output hash, and in the preimage attack, the attacker tries to find out the message input from the hash outcome. Thus, the SHA-256 function is well admitted for ensuring the genuine role of data and its authenticity in different security operations.
The SHA-256 encryption application is in numerous cryptographic protocols, digital signature, certificates authority, and data integrity systems.
The security feature of cryptographic hash function is its robustness and efficiency, which makes it a bedrock of modern cryptography techniques, turning it to be a reliable solution for data security and verification in the majority of applications.
How does it Work?
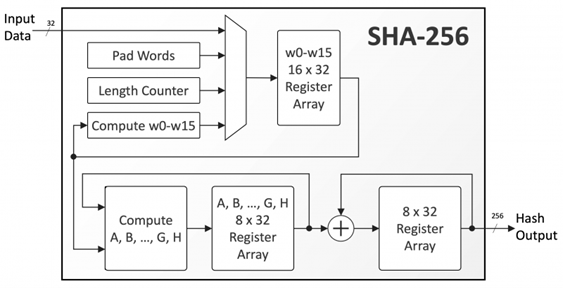
The SHA-256 algorithm works as follows:
Data Preprocessing:
The input data is padded and doubled to be a multiple of 512-bit in length. This is done by using a 1-bit followed by zeros, and then prepending the length of the original message in terms of bits
Message Expansion:
The input block of 512 bits is cut into 16 32-bit words.
Finally, these 16 words are elaborated into 64 32-bit words due to a sequence of logical operations that take place.
Message Compression:
The expanded 64-word message block is then processed through a series of 64 rounds, each involving several steps:
- Determine the round constant: Every round makes use of a different 32-bit constant value that acts as an input based on the position of the process.
- Calculate the message schedule: An output of a 64-entry message schedule is created using the round constant and the message block of 64 words.
- Update the working variables: The working variables, which hold the message schedule and logically operate, are 8 32-bit words stored to intervene in the hashing process.
Calculate the Hash Value:
At last, locating all the working variables at the end of the 64 rounds, their values are mixed in order to present a definite output.
Features & Benefits of Sha-256
The key features and benefits of the SHA-256 algorithm are:
Cryptographic Hash Function:
The SHA-256 is a type of cryptographic hash function, which generates the fixed one of 256 bits of the output(hash value) depending on the input(message).
Recommended: SHA1 Vs. SHA256 – What’s the Difference Between the Two Hash Functions?
The hash value which is unique to each unique input only looks random and is very hard to re-engineer backwards, to the original message.
Fixed Output Length:
SHA-256 provides a 256-bit (32-byte) hash value without fail so that the data can afford an easy comparison and checksum validity.
Data Integrity:
Every time you have a context switch like you enter a different character, there will be a remarkably different hash value produced this way the detection of data tampering becomes easy.
Security:
With 256-bit output size, the number of potential hash values is way huge; thus, brute-force attacks become incomprehensible processes.
Recommended: SHA 256 vs SHA 512: Key Encryption Algorithms Differences Explained!
SHA-256 is designed as a one-way function that is resistant to reversal-engineering schemes of determining the initial input from the end result of hash output.
Efficiency:
However, SHA-256 is comparatively easy to work with and much faster since the generated hash values allow for a high level of data manipulation.
Widespread Adoption:
Now – SHA-256 is the major contributor of safe ceremony, since it is used definitely in many security measures, among them digital signatures, password authentication and the blockchain.
Steps in SHA-256 Algorithm
The key steps of SHA-256 Algorithm are:
Padding Bits: They begin by sandwiching a single ‘1’ followed by as many zero bits as required to have a multiple of 512 bits, as the total length of the padded message.
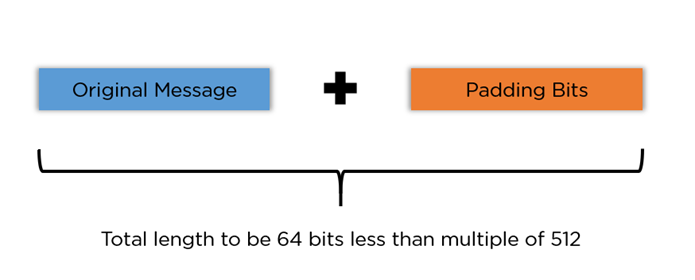
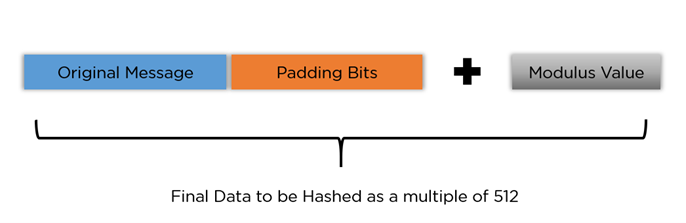
Append Length Bits: The 64 bits are added to the end to represent the original message length in bits.
Initialize Buffers: Five 32-bit buffers (a, b, c, d, e) are initialized to predefined values at the beginning.

Compression Function: The padded message may be then divided into 512 -bits blocks. Every block after 64 rounds undergoes operations such as addition, logical functions, and word rotation. In the end, a 256-bit hash output is garnered.
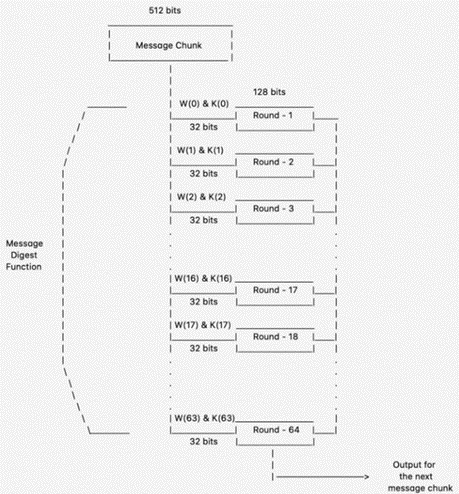
Output: While passing through all the 512-bit stages, the final 256-bit hash value is obtained by combining the eight buffers’ values.
SHA-256 algorithm is a sophisticated function designed for data security and one-way hashing which can be used in digital signatures and all cryptographic applications.
Use Cases/Applications
The key use cases and applications of the SHA-256 algorithm are:
Digital Signatures:
The hashing algorithm SHA-256 is used to produce an exclusive fingerprint (hash value) for the signed object being signed.
Subsequently, the hash value is encrypted by the private key of the signer in order to generate a digital signature.
Recommended: Digital Signature vs Digital Certificate
Recipients can check the signature by deciphering it using a public key and comparing the result hash value.
Password Hashing:
Instead of keeping the passwords in plaintext, organizations now encode them using a hashing algorithm called SHA-256 and store the resulting encoded values.
With each password submission, the system actually calculates the hash and then compares the hash to the stored hash in order to authenticate the user.
Blockchain and Cryptocurrency:
Blockchain algorithms such as Bitcoin, Bitcoin Cash, and Bitcoin SV use the SHA-256 algorithms for a variety of tasks like transaction approvals.
The SHA-256 algorithm holds the security and integrity lamp of a blockchain ecosystem.
Secure Communication Protocols:
SHA-256 is commonly used in SSL/TLS, IPsec, SSH, and PGP which is for gaining data integrity and authenticity.
Data Integrity Verification:
The hash value generated by SHA-256 algorithm allows for the confirmation that data is original and had not been changed as the same input would generate the same hash value.
These examples show us an implementation of SHA-256 algorithm for cybersecurity, data protection, and cryptography by the field.
What are the Characteristics of the SHA-256 Algorithm?
Based on the search results provided, the key characteristics of the SHA-256 algorithm are:
Cryptographic Hash Function:
SHA-256 is a cryptographic hash function that converts, bit for bit, the input of a given message into a fixed-size, 256-bit output (hash value).
Recommended: 128 Bit Vs 256 Bit SSL Encryption Algorithm Explained
In every case, the input will have a unique hash value, which does not look as a-random, hence making it nearly unmanageable to regenerate the initial text.
Fixed Output Length:
SHA-256 generates hash values with each of them being constant and of 256-bit length (32 bytes). Such hash values assure efficient data comparison and integrity verification.
Data Integrity:
Obviously, any change of one dot to the input data, even one character, changes the hash value to a completely different one, and this is how the data authentication is made possible.
Security:
When compared to the traditional 128-bit output size, 256-bit output size gives a much large number of possible hash values, which makes hacking almost impossible.
Recommended: Encryption Vs Hashing Vs Salting – What’s the Difference?
SHA-256 has the desired feature of a one-way function that allows no one to be able to reconstruct the original, the input, from the hashed output.
Efficiency:
Besides its intricacy, hash function 256 – SHA-2 is computationally efficient, the hash values generation becomes easy and fast in order to meet data processing requirements.
Deterministic:
The SHA-256 algorithm is deterministic, relying on the same input, it will always generate the same output.
Widespread Adoption:
SHA-256, owned by a great number of protocols and applications range from encryption via digital signature, authentication of passwords and distributed ledger systems.
Here specified characteristics of SHA-256 algorithm, being consistent and resistant to the chosen data hacks, make it a robust and reliable tool of data encoding in the digital world.
Conclusion
Instill website security to the core of your business and build visitors’ confidence with SSL/TLS encryption requirements by CheapSSLWEB.
We provide low-priced SSL certificates that ensure robust protection against cyber threats and enable data transfer between your site and its users that is both confidential and accurate. You not only nail your site security to HTTPS, but you as well increase its search ranking and user experience.
