RSA vs. AES Encryption: Key Differences Explained
RSA Vs AES Encryption: Technical Differences Decoded
When discussing data communication on the Internet, we can use AES and RSA as fine examples of data encryption. AES stands for Advanced Encryption Standard, while Rivest, Shamir, and Adleman are the names behind the acronym RSA. Being popular data encryption methods, there is always a debate on AES Vs. RSA, and naturally so! However, the technicalities between the two make them distinct and popular encryption methods.
To understand RSA Vs. AES encryption lets us get into the depth of each encryption method. Let’s get started with RSA.
How does RSA Encryption Work?
The RSA algorithm secures the data transmission. Widely used for securing data, it is one of the first practical public-key cryptosystems. The RSA algorithm is based on the fact that it is very difficult to factorize a large composite number into its prime factors.
The RSA algorithm involves three steps. They are:
Key Generation: After generating 2 large prime numbers, they are multiplied. The RSA algorithm keeps the two primes secret while making their product public. It also chooses another number called the public exponent.
Encryption: The sender searches for the recipient’s public key to encrypt a message. The public key contains the product of the primes and the public exponent. After finding the public key, the sender raises the message to the power of the public exponent, modulo the product of the primes. This process encrypts the message.
Decryption: To decrypt the data, the RSA algorithm uses the two primes and a private exponent. The recipient raises the encrypted message to the power of the private exponent, modulo the product of the primes. This process decrypts the message.
Many different applications use the widely-used RSA algorithm. Some common use cases of RSA include:
● Secure Communications
People often use RSA to encrypt messages both in transit and at rest. For example, the Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols maintain the security of communications that take place on web browsers and servers and key exchange, too by using RSA.
● Digital Signatures
RSA has the capability to create digital signatures that people can use to verify the authenticity of a message. When specific information is encrypted using a private key, the recipient can validate it. Indeed, the owner of the corresponding public key has sent it. To verify the authenticity of a message, the RSA algorithm decrypts the data using the public key.
● Software Protection
People can use RSA to protect software and other digital content by encrypting it with a private key and requiring the user to provide a corresponding public key to decrypt and use the software.
● Secure Authentication
Systems that require users to prove their identity can use RSA to secure authentication. For example, in a two-factor authentication system, a user might enter a password and also prove possession of a private key by signing a challenge sent by the system.
● Secure Payments
RSA is also used in many payment systems. Banks and other financial institutions use RSA to ensure secure transactions and payments.
● Encryption and Email Signing
Most of the email-based services and programs leverage RSA for encrypting the message content and signing the emails. Thus, only the intended recipient is capable of reading them and they know that the recipient is certain that it was sent by a legit sender.
Read also about What is an RSA Certificate? How RSA Certificate Works?
Now let us check how AES works.
How does AES Work?
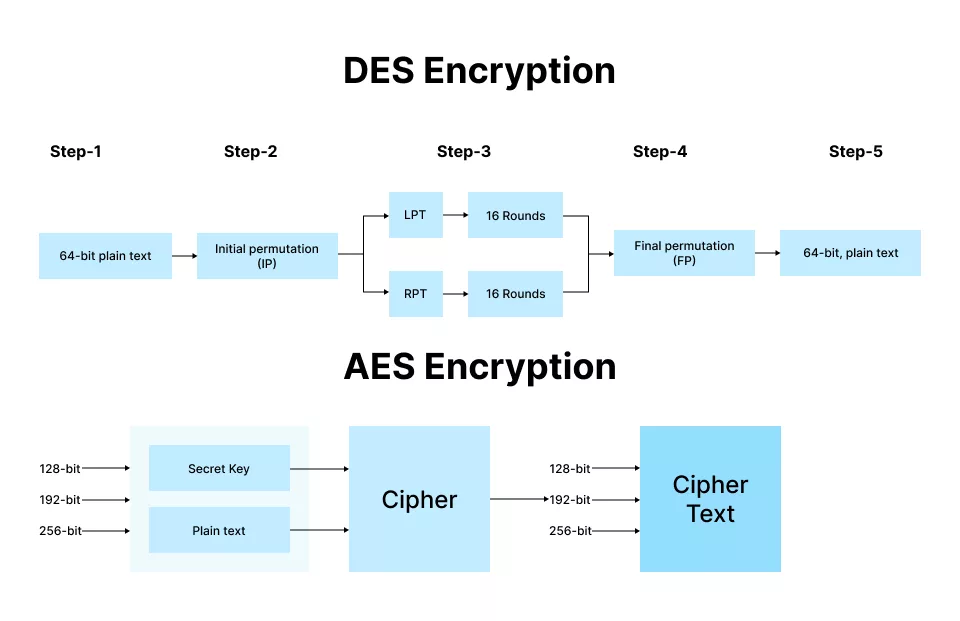
AES is a symmetric key encryption algorithm. Unlike RSA, which uses a pair of public and private keys, AES employs one key for encrypting and decrypting the data.
The AES algorithm works by taking a plaintext message and then applying a series of mathematical operations to it, called rounds, based on a fixed-length key. 128 bit, 192-bit, and 256-bit are AES key lengths. The more rounds and the larger the key size, the more secure the encryption. Each round applies a different, unique set of mathematical operations on the data, making it extremely difficult for an attacker to break the encryption.
AES encryption is used in a wide variety of applications due to its security, speed, and wide adoption. Here are a few examples of where AES encryption is used:
● Wireless Networks
AES encryption is used in the security protocols of wireless networks, such as WPA and WPA2, to protect the wireless traffic between devices and the wireless access point.
● Virtual Private Networks (VPNs)
AES is often used to encrypt the traffic sent over VPNs, which allows remote users to securely access a private network over the internet.
● File Encryption
AES encryption is used in many file encryption and compression tools, such as WinRAR and 7-Zip, to securely encrypt files and protect them from unauthorized access.
● Cloud Storage
AES encryption is often used to encrypt data stored in the cloud, to protect it from unauthorized access and to comply with regulatory requirements.
● Hardware Security Modules
AES encryption is used in hardware security modules (HSMs), which are specialized devices used to secure cryptographic keys and perform cryptographic operations.
● Secure Shell (SSH)
AES encryption algorithm is also used to encrypt data sent over SSH, which is used to securely access remote servers.
Other general encryption uses include security protocols and standards such as IPsec, SSL, TLS, and encrypting disk partitions, mobile devices, and other storage media.
Now lets us get into the differences between AES and RSA encryption methods.
What is the Difference Between AES Vs. RSA Encryption?
AES and RSA are two widely-used encryption algorithms. Here are some parameters in which we have explained AES Vs. RSA encryption. Though both algorithms secure data, they are used in different ways and for different purposes. Let’s discuss RSA Vs. AES.
● Encryption Algorithm
AES is a symmetric key algorithm, which means that only one key is employed for encrypting and decrypting data. It can be used with key sizes of 128, 192, or 256 bits. Apart from that, AES is considered to be a secure and fast encryption algorithm and is widely used in various areas like including VPNs and disk encryption software.
RSA, on the other hand, is an asymmetric key algorithm, which means that it uses a pair of keys, one that encrypts and one that decrypts. The encryption key, also called the public key is freely distributed, while the decryption key, or private stays confidential. RSA is commonly used in digital signature and key exchange, such as SSL/TLS used in https.
● Encryption Process
Another key difference is that AES is a block cipher which means it encrypts the data in fixed-size blocks (128 bits), while RSA is a public-key encryption system, RSA encrypts the session key that is used to encrypt data instead of the data itself.
● Use Cases
While RSA is widely employed for key exchange or digital signature, AES is mainly used for data encryption. The latter is faster and more efficient than the former. However, RSA is generally considered to be more secure for digital signature and key exchange because it is done on the basis of the difficulty of factoring large numbers.
For a better understanding of RSA Vs. AES encryption, refer to the table below.
| RSA | AES | |
| Type of Crypotography | Asymmetric | Symmetric |
| Application of keys | Different keys are used for the purpose of encrypting and decrypting data | For the encryption and decryption of data one same key is used. |
| Security | Low | High |
| Block Size | Minimum 512-bit | 128-bit |
| Key Length | 1 | 10–128 bits, 12–192 bits, 14–256 bit |
| Security | Less Secure | Highly Secure |
| Speed | Slow | Fast |
AES Vs. RSA
RSA and AES are both encryption algorithms. However, they are used for various purposes and have some key differences. In summary, AES is good for encrypting data, while RSA is good for digital signature, key exchange or encryption/decryption of symmetric keys like AES.
Read also about SSH Vs. SSL – The Technical Differences Explained