Top 10 SSL Certificate Security Best Practices

What is SSL (Secure Sockets Layer)?
SSL, which is an abbreviation for the Secure Sockets Layer, is a cryptography technology which acts as a defense mechanism for communication over the Internet.
Hence, it implements a safe communication channel between the web server and client’s browser, which prevents the information that is transmitted from the third party’s intrusion.
Recommended: Encoding Vs. Encryption: Explaining the Difference
SSL encoding system makes securing data by avoiding unwanted access and eavesdropping on sensitive information easier by malicious actors.
This is done through encrypting personal information like login credentials, personal details, and financial transactions. Now it is used by anyone who wants to secure online transactions, including exchanging information of a personal nature.
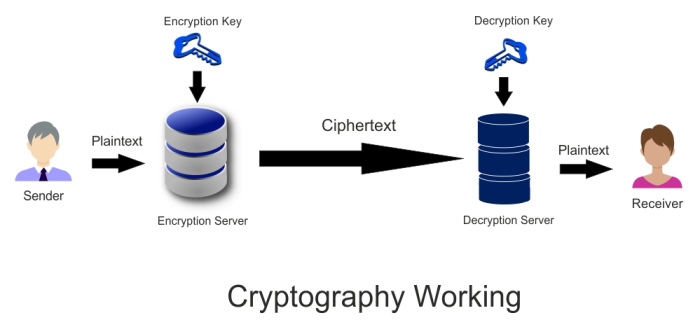
In the transmission process digressing through the network symmetric encryption, it is used to encrypt data which results in only the intended recipient who has already been provided with the decryption key can be able to decrypt and read the encrypted information.
Furthermore, SSL implements asymmetric cryptography for key exchange purposes, allowing two parties (client and server) to come to agreement over encryption keys with absolute secrecy.
SSL (Secure Sockets Layer) certificates are magical elements which are responsible for SSL (Secure Sockets Layer) protocol for the purpose of identifying and verifying the identities of servers and websites.
Recommended: What is an SSL Certificate? Purpose, Benefits & Use Cases of SSL Certificates
Such digital certificates, usually issued by certified Certificate Authorities (CAs), do prove that the website is legitimate and connect server and the client browser with confidence.
When a user visits a web page protected by SSL they use their browsers to verify the security of the certificate and encryption to protect the data transmitted from that site.
What is SSL Security?
SSL (Secure Sockets Layer) is a security mechanism through which information on a network is kept private and the parties involved in the communication can be authenticated and data is not altered.
It was first introduced by Netscape during the year 1995 and then later developed into what is known now as Transport Layer Security (TLS).
SSL ensures a safe channel between the server and client (as a rule, a web browser and a web server) with the help of encryption algorithms for protecting data transfer.
SSL uses two different encryption techniques: neither cross-sectional nor axial- symmetrical. Asymmetric encryption is performed using two distinct matrices, a public key and a private key, for encryption and decryption.
This key is used to encrypt the message which can be decrypted by the other key only. The process can be reversed and that’s how data is secured between two parties.
Recommended: Symmetric Encryption vs Asymmetric Encryption
While the symmetric encryption uses one shared key (either a key pair or a single key) to encrypt and decrypt the message, the asymmetric encryption involves the use of separate keys for different parties.
Setting up an SSL connection would require the site owner to buy an SSL certificate from a Certificate Authority (CA) and then install it on the site.
During the process of the visitor on the web browsing the website, the browser and the web server communicate through SSL and a technique called the SSL/TLS handshake.
Recommended: How to Fix the SSL Handshake Failed Error?
Here the process deals every time with important components: keys exchange, server identity verification and how the encryption will be done.
So, once the SSL connection is made, all the communications or transfers between the client and the server are encrypted.
Of course, this is done with a focus of reserving the sensitive and critical information being sent around like the login credentials and the credit card details.
Encrypting data goes hand-in-hand with the protection of the information as any changes done to the data cannot be done when in transit.
Best Practices to Secure SSL Certificate
SSL certificates are the individual keys which in turn are essential for safe handling of data which is sent through the internet.
Ensuring that best practices are followed in the security of SSL certificates is a critical action that needs to be put in place to deal with the numerous risks that come with cyber threats and to maintain loyalty among users.
Here’s a detailed explanation of each best practice:
1.Choose a Trusted Certificate Authority
Primarily, the first action is to make a decision as to the Certificate Authority (CA) that is reputable and trusted in order to get the SSL certificates. CAs issue digital certificates that conform to that of the website or server.
Recommended: What is a Certificate Authority (CA) in PKI? How Does Certificate Authority Work?
Security should be a key factor, select an accountant that has the latest security framework, is following the appropriate protocols, and that has a history of stability.
2. Use Strong Encryption Algorithms
SSL certificates apply the encryption algorithms to ensure data confidentiality transmission vs. internet.
It is important to implement SSL certificates that use cryptography families RSA (Rivest-Shamir-Adleman) or ECC (Elliptic Curve Cryptography) with key lengths of 2048 bits or more make sense.
Huge encryption makes it possible to protect data from brute-force assaults and decryption operations via its strength.
3. Enable HTTPS Protocol
HTTP Secure (HTTPS) can encrypt communication between web servers and computers of the browser users, preventing attacks from intruders against data during the moment of exchange.
Recommended: Port 80 (HTTP) vs. Port 443 (HTTPS): Major Difference to Know
Regulating the use of HTTPS ensures that sensitive personal details like login credentials, personal data and financial data should be encrypted during interacting with the third-party server in a way that it can never be eavesdropped or manipulated.
4. Implement Extended Validation (EV) Certificates
Extended verification SSL certificates offer the most sophisticated authentication and trust procedures, with the ability to validate the genuine identity of the website owner.
Recommended: 7 Cheap Extended Validated (EV) SSL Certificates
The creation of EV certificates is important since it is one of the ways that the website is identified in the browser’s address bar. Thus, it enhances visibility and as a result proves real company status.
5. Regularly Update SSL/TLS Protocols
SSL/TLS protocols are upgraded with a view to eliminating accepted security loopholes and well known gaps. It is crucial to keep track of the latest versions of the SSL/TLS protocol, e.g., TLS 1.2 or later, to maintain confident communication through servers and clients.
The emergence of more recent protocol upgrades is supposed to eliminate the bad outcomes often caused by insecure older algorithms and their cracks.
6. Enable Perfect Forward Secrecy (PFS)
Perfect Forward Secrecy (PFS) helps in creating non-reproducible session keys for every single encrypted connection which in turn significantly enhances the secureness level of SSL connection.
This makes it a desirable mechanism as a compromised server private key leads neither to decryption prospect nor to the interception of data.
Capabilities for PFS protect the data from cyberattacks and provide the privacy against accessing the confidential data during transport over the Internet.
7. Implement Certificate Revocation Checks
CRL and OCSP responses are the methods that allocate information about the certificates being misused. The servers ought to do consistent checks on CRL and OCSP to see whether the certificates expired or are revoked already.
Discarded or invalid certificates should be immediately replaced for encryption of secure connections keeping SSL throughout integrity.
8. Utilize Multi-Factor Authentication (MFA)
MFA (Multi-Factor Authentication) ensures an additional protective skin by requiring the accessors to validate through multiple factors including One-Time password (OTP) or biometric data authentication.
By Implementing MFA we would be able to stop issues related with issuing or revoking certificates so as to mitigate the impact of certificate abuse or leakage.
9. Secure Private Key Management
The certification authorities must adequately secure the private keys of SSL certificates and avoid accidental events that result in the compromise of such keys.
Recommended: Public Key and Private Key Pairs: What are they and How do they Work?
Organizations need to exploit encrypted key vaults or the protection of private keys in secure hardware devices, create robust controls about access to them and regularly audit and monitor them to ensure that the confidentiality and integrity of information are upheld.
10. Regularly Renew SSL Certificates
Keeping a watch on SSL certificate expiration dates and making timely renewals of certificates is an essential process for protecting against the service disruptions that arise from unintended certificate expiration and the curtailing of continuous security coverage.
Recommended: Renew your SSL/TLS Certs – Starts at Just $3.99/Yr
Automating renewal ceremonies and setting up a certification expiry alert is a way to maintain the validity of the SSL certificates through time and avoid security breaches.
Conclusion
CheapSSLWeb is a well known SSL/TLS certificate provider which cheaply and reliably supplies SSL certificates from common Certificate Authorities such as Comodo, Sectigo, Certera, RapidSSL, Thawte, GeoTrust and DigiCert.
Buy Cheap SSL/TLS Certs from CheapSSLWEB – Starts at $3.99/yr
